What is a DMARC Record? Improve Email Security
DMARC (Domain-based Message Authentication, Reporting and Conformance) is a technical standard that helps protect email senders and recipients from spam, spoofing, and phishing. The DMARC record allows easier to identify spam and/or phishing messages, received in the customer's mailbox, and to keep them out of there.
Implementing a DMARC record not only enhances email security by preventing unauthorized use of your domain but also improves the overall deliverability of legitimate emails. By specifying policies for handling suspicious emails, DMARC helps maintain your domain's reputation and ensures that your messages reach your customers' inboxes safely.
Example of DMARC record:
| Host | Type | Points to: | TTL |
| _dmarc.yourdomain.com | TXT | v=DMARC1;p=reject;pct=100;rua=mailto:mailmaster@postmaster.com | 3600 |
In the example shown above, the sender requests that the receiver outright reject all non-aligned messages and send a report, in a specified aggregate format, about the rejections to a specified address. If the sender was testing its configuration, it could replace “reject” with “quarantine” which would tell the receiver they shouldn’t necessarily reject the message, but consider quarantining it.
DMARC records follow the extensible “tag-value” syntax for DNS-based key records defined in DKIM.
You can see the available tags here:
| Tag name | Purpose | Sample |
| v | Protocol version | v=DMARC1 |
| pct | Percentage of messages subjected to filtering | pct=20 |
| ruf | Reporting URI for forensic reports | ruf=mailto:authfail@example.com |
| rua | Reporting URI of aggregate reports | rua=mailto:aggrep@example.com |
| p | Policy for organizational domain | p=quarantine |
| sp | Policy for subdomains of the OD | sp=reject |
| adkim | Alignment mode for DKIM | adkim=s |
| aspf | Alignment mode for SPF | aspf=r |
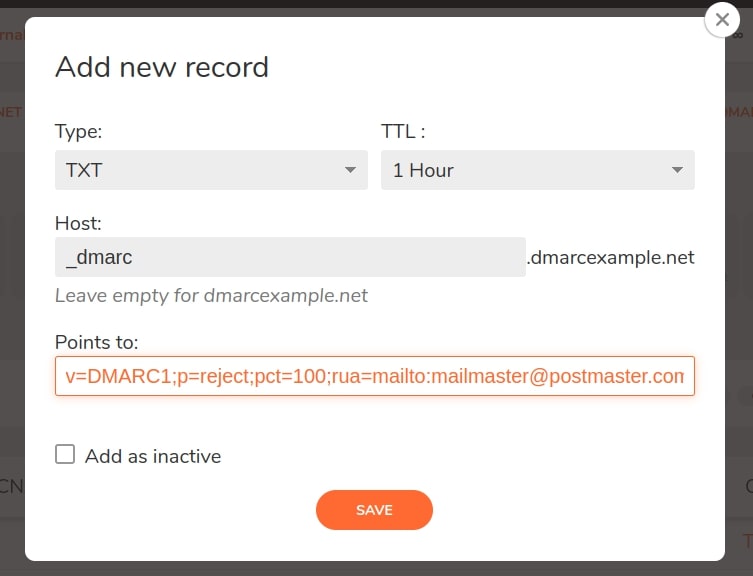
To add DMARC, you need to create a TXT record in your DNS Zone. You can see the example below:
How does DMARC record work?
A DMARC policy allows a sender to indicate that their messages are protected by SPF and/or DKIM, and tells a receiver what to do if neither of those authentication methods passes – such as junk or reject the message. When an inbound mail server receives an incoming email, it uses DNS to look up the DMARC policy for the domain contained in the message’s “From” (RFC 5322) header. The inbound server then checks evaluates the message for three key factors:
- Does the message’s DKIM signature validate?
- Did the message come from IP addresses allowed by the sending domain’s SPF records?
- Do the headers in the message show proper “domain alignment”?
With this information, the server is ready to apply the sending domain’s DMARC policy to decide whether to accept, reject, or otherwise flag the email message.
After using DMARC policy to determine the proper disposition for the message, the receiving mail server will report the outcome to the sending domain owner.
Why do you need a DMARC record?
DMARC is the latest trend in email authentication techniques. It helps protect domains from being spoofed and from fraudulently sent emails. DMARC is a free and open technical specification that is used to authenticate an email by aligning SPF and DKIM mechanisms. This is why DMARC is used only if SPF and DKIM records are already added to the DNS for your domain name. Here are the main reasons why to implement it:
- Enhanced Security: DMARC adds an extra layer of security by ensuring that both SPF and DKIM are correctly aligned, significantly reducing the risk of email-based attacks.
- Improved Trust: Implementing DMARC helps build trust with your recipients by confirming that your emails are legitimate, thereby improving your domain's reputation.
- Visibility and Reporting: DMARC provides detailed reports on email authentication, giving domain owners insight into potential abuse and helping secure their email ecosystem even further.
How to create a DNS DMARC record?
To add DMARC, go to your DNS zone management page and click on “Add new record”. For "Type" select "TXT" and type as follows:
- Type: TXT
- TTL: 1 Hour
- Host: _dmarc*
- Points to: dmarc tags and values.
*This hostname is used as an example.
How to add a DMARC Record - Step by Step video:
How to start managing DMARC records for your domain name?
- Open a Free account from here - it is free forever
- Verify your e-mail address
- Log in to your control panel
- Create a new DNS zone from the CREATE ZONE button - read more here
- Add the DMARC records you need as it is described in this article
Best practices for DMARC record configuration
Some best practices for DMARC record configuration include:
- Configure SPF and DKIM properly.
- Review DMARC reports and address suspicious messages.
- Maintain a list of verified senders.
- Set up custom alerts for suspicious activity.
Additionally, you should review your records every time you make changes to your mailbox settings to ensure that any new changes are implemented correctly.
How to check my DMARC records?
We will show you how you can check your DMARC records if they are visible in the DNS using different commands:
- To check the DMARC record with Dig, open the Terminal application. Type the following command:
$ dig _dmarc.cloudns.net TXT
You need to replace “cloudns.net” with the domain you want to query. In addition, keep in mind that TXT must be specified as the type of record that you are looking for at the end of the command.
- To check the DMARC record with Nslookup, open a command line. Inside, type the following command:
$ nslookup -type=TXT _dmarc.cloudns.net
Again, replace “cloudns.net” with the domain you want to query. After running the command, you should see a DMARC record and any errors or warnings associated with it.
- To check the DMARC record with the Host, open a Terminal application. Then, write the following command:
$ host -t txt _dmarc.example.com
Press Enter and check the results!
Furthermore, to check DMARC records, you could use an online DNS record lookup tool such as the ClouDNS Free DNS tool.
DMARC report - what is it?
DMARC reports are generated by inbound mail servers as part of the DMARC validation process. There are two formats of DMARC reports:
- Aggregate reports, which are XML documents showing statistical data about the messages received that claimed to be from a particular domain. Date reported includes authentication results and message disposition. Aggregate reports are designed to be machine-readable.
- Forensic reports, which are individual copies of messages which failed authentication, each enclosed in a full email message using a special format called AFRF. Forensic report can be useful both for troubleshooting a domain’s own authentication issues and for identifying malicious domains and web sites.
Support of DMARC records
ClouDNS provides full support for DMARC records for all our DNS services, including the listed below. Just write to our technical support, if you need any assistance with your DMARC records configuration. Our Technical Support team is online for you 24/7 via live chat and tickets.
FAQ
Question: Where is the option for adding a DMARC record? I cannot see it.
Answer: DMARC can be implemented by adding a TXT record, as described in this article.
Question: How can I generate the values for my DMARC record?
Answer: There are plenty of DMARC generators and DMARC wizards on the Internet. You can use any of them or DMARC record generator by ClouDNS.
Question: What types of policies can I set with a DMARC record?
Answer: You can set three main types of policies with a DMARC record: none, quarantine, and reject. These policies can be used to determine how email platforms should handle emails from a particular domain.
Question: What should I do if I find suspicious activity on my DMARC reports?
Answer: If you find suspicious activity on your DMARC reports, you should immediately address the issue by setting up a more restrictive policy or tightening security on your domain. Additionally, you should also report the issue to the email address provided in the reports.
Question: How often should I review my DMARC record?
Answer: You should review your DMARC record whenever you make changes to your mailbox settings, as this will ensure that any new changes are properly implemented.
Last modified: 2025-03-26