Yes, the Smurf attack sounds cute and harmless, but we can assure you it is not. Instead, it is yet another DDoS attack that is made to damage businesses and disrupts their workflows.
Table of Contents
Smurf attack definition
The name Smurf comes from a popular Belgium comics and cartoon with the same name. There are many small blue characters in it who work together to bring down one big bad magician.
The Smurf DDoS attack is a protocol-based DDoS attack that uses the popular Internet Control Message Protocol (ICMP) to send ping packets of data with a spoofed IP address of the source, thanks to malicious software.
The packets are sent to a computer network using an IP broadcast address. The devices on that network will respond and send answers to the IP address. The fact that not only one computer but a whole network of computers respond to the victim’s IP address leads to a substantial amplification and potentially huge traffic towards the victim. So strong that it could severely slow down the victim’s computer and even bring it down for a while.
And you know, downtime means losses for the business.
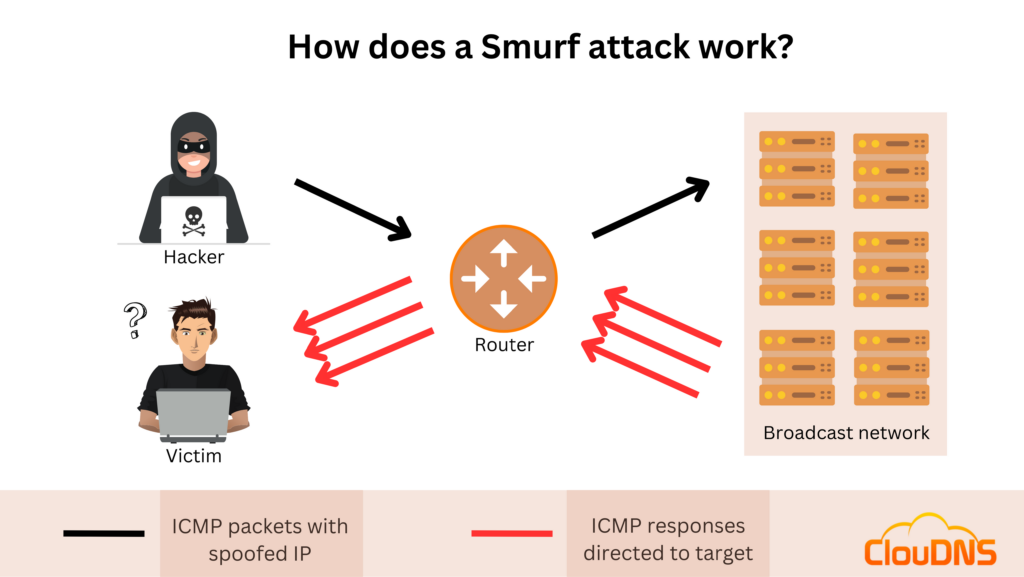
How does a Smurf attack work?
- The malicious Smurf software spoofs the packets’ IP address and replaces it with the victim’s IP address. That way, all the traffic will go to it.
- The packets of data are sent to a broadcast IP address of a router. That way, the router will send the message to all the connected devices inside this broadcast network, and the attack will get amplified many times. So many times as there are devices that respond.
- Each of the devices will receive the packets of data. They will respond but to the spoofed IP address (the target’s IP address). So the traffic will go directly to the victim.
- The target starts to receive packets of data that it didn’t ask for. One after another, and if there are too many, the target starts to have problems processing them. Eventually, if the intensity does not go down, the target will be unable to process the pings and be overwhelmed.
What is the history of Smurf attacks?
Dan Moschuk (a.k.a. TFreak), a popular hacker at the time, created the original code for the malware in 1997. Dan was still an adolescent at the time. He sent the original software to some of his friends, and later the smurf.c crashed various IRC servers.
Because of the Smurf attack, network equipment producers started to change the settings of their devices and limit broadcasting to only inside the LAN.
Some years later, TFreak continued his work in malicious software and created a UDP version of the Smurf attack and called it Fraggle.c.
Types of DDoS Smurf attack?
There are two main types of Smurf attack:
Basic Smurf attack
The Basic Smurf attack works, just as we explained to you, flooding a network with ping packets that have spoofed the IP address of the victim. Then, all the devices on the network answer the packets and send the answers to the target, causing massive traffic that can bring down the system over time.
Suggested article: What is flood attack?
Advanced Smurf attack
It looks similar to the Basic Smurf attack but with a small difference. The Advanced can spoof the IP addresses of the packets in a way that it can send the response to more than one target. When the attackers have infected enough networks, they can use this amplified traffic to multiple victims to cause more damage.
How do you detect it?
Detecting a Smurf attack can be a difficult task. ICMP monitoring is a crucial tool when it comes to catching this attack. ICMP is an Internet Control Message Protocol that sends an alert if it detects an attack. This type of monitoring allows for real-time analysis of any suspicious activities, allowing for faster detection and mitigation of any damage caused by a Smurf attack. To set up ICMP monitoring, it is essential to set a threshold based on your network’s typical performance. Once a traffic spike that exceeds the threshold is detected, your IT team can act accordingly. ICMP monitoring provides an efficient and effective way to detect a Smurf attack promptly.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
How to mitigate Smurf DDoS attack?
There are 3 things that you can do to mitigate a Smurf attack:
Use DDoS protection
Having a large network of servers means your servers can resist stronger traffic. When you combine it with an intelligent traffic monitor that can find the malicious traffic and a network of scrubbing centers, you will have excellent protection against this type of DDoS attack.
If you want to try it out, you can see our DDoS protection plans right here. Stay safe and keep your business running, lowering the downtime to a minimum.
Forbid the ICMP traffic
You can use your firewall and stop the ICMP traffic completely. This will make it impossible to suffer a Smurf attack or any other DDoS attack based on the ICMP. The problem is that you won’t be able to use a ping command for diagnostics. This could be problematic for administrators who need to check if all of the devices on a network or remote servers are connected and working, so this might not be an option for most people.
Stop packets with a broadcast IP address
You can also set up all your hosts and routing devices to ignore packets that have a broadcast IP address. That way, even if a modified Smurf attack packet gets to your network, it won’t be allowed. If you don’t need to broadcast any other messages, this could be an option. Still, it will limit your configuration, and you might need this feature.
Smurf attack Transmission
The Smurf attack can start from a Trojan horse or malware. It can be downloaded by somebody on the network and executed, or it can be in the form of an application. It is important to educate your staff about the dangers of phishing attacks that can lead to such problems.
The smurf will remain hidden, on the infected host, for a long time until the attack needs it. Then he or she will activate it, and the process of generation of ICMP packets with a spoofed IP address will start. They will be targeted at the victim, and the DDoS attack will start.
Impact of Smurf DDoS Attack
A successfully executed Smurf DDoS attack can cause severe and far-reaching damage. That is why it is important to be aware of the potential consequences.
- Service Disruption: The primary goal of a DDoS attack, including Smurf attacks, is to disrupt the availability of services. By flooding the victim’s network with traffic, legitimate users are unable to access essential services, leading to downtime and potential loss of revenue.
- Resource Exhaustion: Smurf attacks can overwhelm network infrastructure, including routers, switches, and servers, leading to resource exhaustion. As a result, the victims can experience degraded performance or even complete system failure.
- Reputation Damage: A prolonged DDoS attack can tarnish the reputation of an organization, corrupting trust among customers and partners. The perception of unreliability and insecurity can have long-lasting consequences for the victim’s brand.
- Financial Losses: The financial impact of a Smurf DDoS attack can be significant. That includes not only immediate costs associated with mitigating the attack but also long-term losses originating from decreased productivity and loss in customer trust.
What is Fraggle attack, and how does it differ from Smurf attack?
The Fraggle attack is very similar to the Smurf attack, as both are Distributed Denial of Service (DDoS) attacks that send massive numbers of echo requests with spoofed source IP addresses. However, the primary difference is that the Fraggle attack involves sending User Datagram Protocol (UDP) broadcast packets over ports 7 and 19, instead of the usual ICMP packets used in the Smurf attack. In other words, while the Smurf attack focuses on flooding the victim’s network with ICMP echo requests, the Fraggle attack spreads the attack traffic across a greater area of the target system.
The goal of both the Smurf and Fraggle attacks is the same — to send an overwhelming volume of data to the server or network, quickly overloading it and causing it to crash or become unusable. However, the Fraggle attack has the advantage of avoiding detection by traditional firewall configurations since UDP broadcast packets are usually allowed by most firewalls. It is also important to note that Fraggle attacks can be used in conjunction with Smurf attacks for an even more significant impact. in conjunction with Smurf attacks for an even greater impact.
What Are the Warning Signs of a Smurf Attack?
Smurf DDoS attacks can be difficult to detect at first, but there are clear warning signs that indicate an ongoing attack. Early detection is crucial to minimize downtime and protect your network.
- Unusual ICMP Traffic Spikes: A sudden and unexpected increase in ICMP echo requests or responses (ping requests) can signal an attack.
- Network Slowness or Congestion: If your network experiences unexplained slowdowns, it may be struggling to process excessive traffic.
- Increased CPU and Bandwidth Usage: Network devices, routers, and servers may show high resource consumption, as they attempt to process a flood of incoming traffic.
- Users Unable to Access Services: Customers or employees may report connection issues, indicating that legitimate traffic is being drowned out by attack traffic.
- Frequent Disconnections or Timeouts: Websites, applications, or VoIP services may keep disconnecting due to overwhelming traffic.
- Suspicious Network Logs: Reviewing firewall or router logs may show a large number of ICMP requests from multiple devices in a short period.
Monitoring tools, firewalls, and traffic analyzers can help spot these signs early. If you notice any of these signs, immediate action is required to mitigate potential damage.
Conclusion
Staying safe online is getting harder every day. But you and your business can still be protected. By learning about threats like the Smurf attack and other DDoS attacks, you can understand how to stay safe. Use DDoS protection, and don’t let bad actors negatively influence the work of your servers.