Table of Contents
What is Ping command?
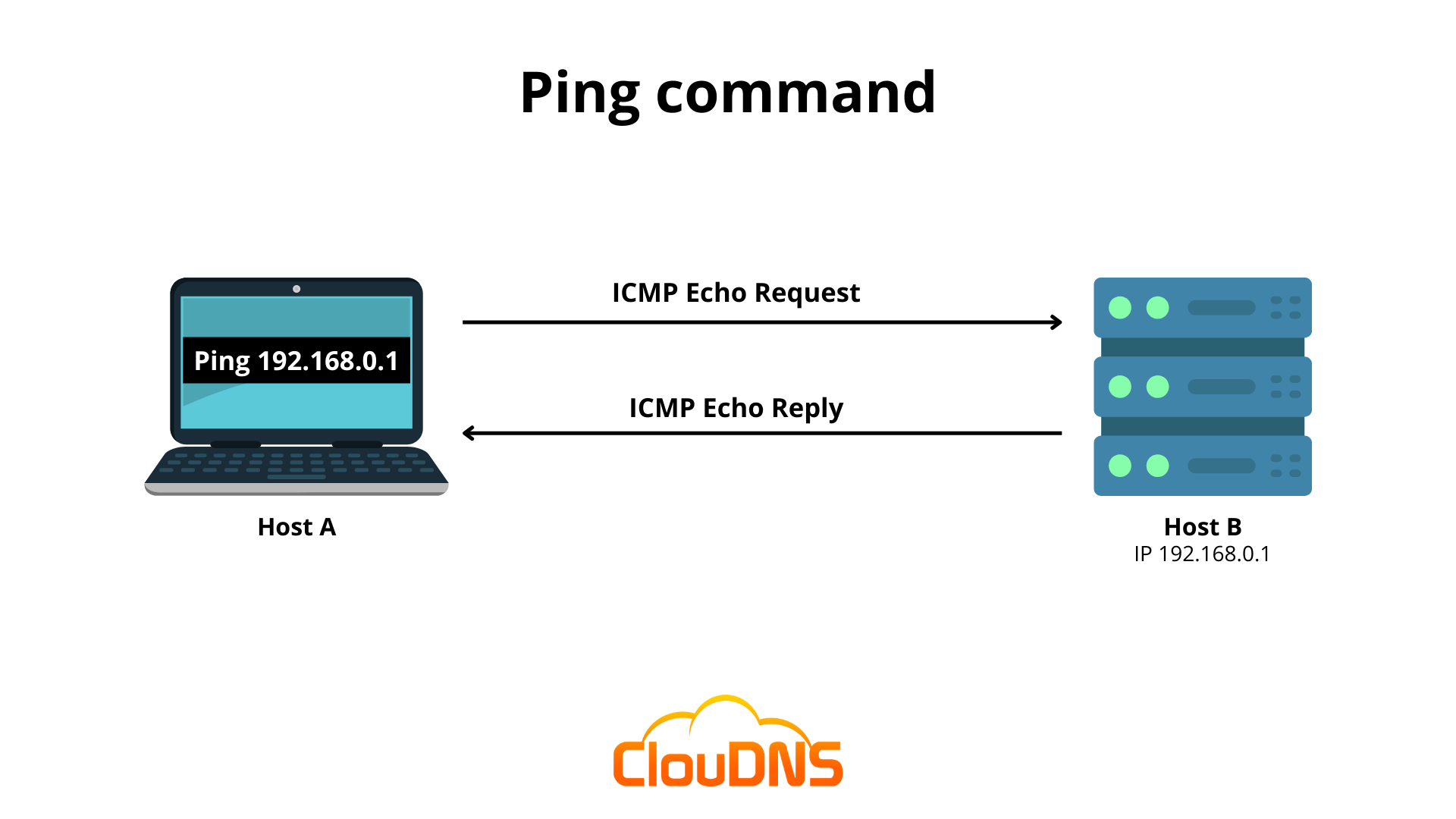
Ping is a very universal command between all the operating systems. You can use it to test if you can reach your target and how much time it will take to do it. Ping sends Internet Control Message Protocol (ICMP) packets to the destination. Then it waits for the echo reply. It can show statistic for this request, errors and packet loss.
When you use this command, you will send few echo requests, usually 4. Then you will receive a result for each of them, that indicates if they were successful, how much data was received, the time it took for the response and TTL (Time to live).
Brief History
The Ping command is a foundational tool in computer networking, tracing its origins back to the earliest days of the Internet. Developed by Mike Muuss in 1983, Ping emerged as a simple yet powerful utility for testing the reachability of a host on an Internet Protocol (IP) network.
Muuss, a respected computer scientist, created the tool while working at the Ballistic Research Laboratory. The name “Ping” itself reflects the sonar concept from submarines, where a pulse is sent to measure the distance to an object. Similarly, the Ping command dispatches small packets of data to a target device, awaiting their return to measure the round-trip time.
Initially implemented for Unix-based systems, Ping swiftly gained widespread adoption due to its effectiveness in troubleshooting network connectivity issues. Over time, it has evolved alongside networking technologies, remaining a staple tool for network administrators, system engineers, and enthusiasts alike. Its versatility extends beyond connectivity testing, serving as a vital diagnostic tool for assessing network performance and identifying potential bottlenecks.
Ready for ultra-fast DNS service? Click to register and see the difference!Experience Industry-Leading DNS Speed with ClouDNS!
How does it work?
Imagine the Ping command as an echo locater. When you use it on your computer, it sends a specific small packet with the ICMP ECHO_REQUEST to its destination (it could be a server, another computer on the network or a router). The recipient must bounce back the message, and send ECHO_REPLY as an answer.
Your computer will always have 127.0.0.1 IP address. If you try to ping it, you will always get fast result. The command will verify that the TCP/IP on your device is working fine.
You can use ping localhost and get the same result since it is the same.
What is Localhost (IP 127.0.0.1)?
If you get 4x Request timed out, then it is not working ok.
How to use Ping command?
You have the ping utility on whatever operating system you have.
On Windows, open the Command Prompt and on macOS and different Linux distros, open the Terminal.
There are small differences in the syntax of the ping command on the OSes. You can see them down below.
You can ping:
- A domain name and see how much time it will take to respond.
- An IP address. It will also show response time, but it will the important part is that it will show that the device is well-connected.
We will try to use it with www.google.com. Write the following:
ping www.google.com
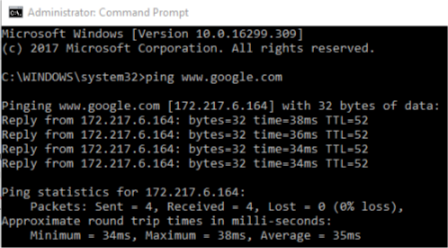
The first part that you will see, who are you pinging, its IP address, and the packet’s size – 32 bytes.
After that, you will get 4 results. Ping sends 4 echo messages unless you specify a different number. Those 4 answers will have response times in ms – milliseconds and TTL value showing the time to live of the packet.
You will also get a few stats – completion rate that shows how many packets managed to arrive and a minimum, maximum, and average time.
Ping switches and variables
There are a lot of small differences when you use ping on Windows and Linux or macOS. For example, the option in Windows is “–n” and in Linux and macOS is “–c”. The best thing you can do is to check the syntax first. You can see all the available variables, switches, and options with a short command.
Ping command syntax for Windows
To get to the list of all possible options for the ping command on Windows, you can write in the Command Prompt:
ping -?
It will give you a result with a full list of options that can make your troubleshooting easier.
| Midifier/Option | What does it do? |
| -t | Constant ping without stopping |
| -a | Resolve an IP address to its hostname |
| -n | Setting the number of echo messages. The default value is 4 |
| -l | Use to send the size of the buffer |
| -f | Stopping the fragmentation of the flag (IPv4-only) |
| -i | Change the TTL value |
| -v | Not functioning any more |
| -r | Use it to see the number of hops and get a record (IPv4-only) |
| -s | A timestamp for each hop (IPv4-only) |
| -j | Loose source route along host-list (IPv4-only) |
| -k | Strict source route along host-list (IPv4-only) |
| -w | Setting the time that your device can wait for an answer |
| -R | Check the reverse route (IPv6-only) |
| -S | Source address to use |
| -c | Routing compartment identifier |
| -p | Ping a Hyper-V Network Virtualization provider address |
| -4 | Use IPv4 only |
| -6 | Use IPv6 only |
Ping command syntax for Linux and macOS
To get to the ping syntax on Linux or a computer with macOS, you need to type this in the Terminal:
ping –h
| Midifier/Option | What does it do? |
| a | Makes a sound when it arrives at the target device |
| b | This lets ping a broadcast IP address. |
| B | Stops the ping from changing the source IP address. |
| c (count) | Set the number of pings. |
| d | SO-DEBUG on the used socket |
| f | Floods the network with many ping packets a second. |
| i (interval) | Interval, in seconds, between successful transmissions. |
| I (interface address) | Defines the source IP address to a particular interface IP address. |
| 1 (preload) | Numbers of echoes sent without waiting for the replies. |
| n | In the output, it shows hostname instead of IP addresses |
| q | A quiet output. One-line ping and summary |
| T (ttl) | T – time to live value (TTL) |
| v | Verbose output |
| V | Check the version of the ping command with it |
| w (deadline) | Time for the exit, no matter the number of messages sent and received. |
| W (timeout) | Waiting for response time (seconds) |
Troubleshooting
- Ping an IP address to see if the device is well connected. If it fails, then the device is not connected at this moment or not reachable over the network we are checking.
- Another scenario is that it is successful but the response times are very long. It means that you or the other side might have problems with the connection.
- You can test different parts of the network to check which are working fine and which are not.
- If you want to check if you are connected to the Internet, you can check one of Google’s IPs, “ping 172.217.6.164”. Why Google you ask? It is just effortless to remember. And do you remember Google been offline? Not really.
- You can use it as a constant checker. Put it with an option to “run until stopped,” and as long as everything is okay, it will continue, but if something fails you will see it immediately.
- If you can’t reach the name, but you can reach the IP address, this shows a problem with the hostname resolution. Probably the DNS servers are not pointed correctly, or they are not accessible.
Monitoring
Ping command appears to be a great tool for monitoring the network availability of different devices. If the command runs as a scheduled task, it can offer simple polling of any network computer or machine. The great thing about it is that it is not necessary to install any additional software or open additional ports.
ICMP Ping monitoring is easy to accomplish due to the ‘run until stopped’ option, which allows the most basic of any up/down monitor. So, whenever the pings start failing, that means there are some difficulties reaching the system.
The ping time, measured in milliseconds (ms), is preferred to be as lower as possible. That is going to indicate the good quality of the ping. In addition, it can deliver signals about the health of your network and its performance speed. Ping monitoring sends an Internet Control Message Protocol (ICMP) echo request. That means when the monitored device receives the request, it replies immediately with the echo reply packets.
Security
Sometimes, a cybercriminal is enough to know that a precise system exists and is connected to the global network to initiate a malicious attack. Thankfully, performing a detailed analysis of the Ping command replies could be extremely helpful. You could perhaps find valuable details, like which operating system (OS) the target is running, where the device is located, and so on.
There are different hacking tools that allow taking advantage of “walking the range.” They use the Ping command for each IP address on a targeted network in order to obtain a list of systems that are reachable and will reply. For that reason, a lot of firewalls are configured in a way that stops Ping requests coming from untrusted networks.
More examples of Ping command (Windows, Linux and macOS)
Here we have a few more use cases of ping command for Windows, Linux and macOS users:
*You can change the IP addresses of the examples or the hostnames and use them with yours. Also feel free to modify the command for your needs.
Interval – ping –i 5 8.8.8.8 (Linux)
This will make it wait 5 seconds before sending the following packet.
Custom number of pings – ping –n 8 google.com (Windows) ; ping google.com –c 8 (Linux and macOS)
You can decide how many echo messages to send.
Check version – ping –V (Linux)
You will see the version of the ping you have.
Flood – ping –f 127.0.0.1 (Linux)
This will flood the network with many pings.
Only Statistic – ping google.com –q (Linux and macOS)
It will show you just the statistic, not each individual ping time.
Change packet size – ping –s 100 google.com (Linux)
It will change the size of the packets. The original is 32 bytes (Windows) and 56 (Linux and macOS), and in this example we have set it to 100.
Timeout – ping –w 20 google.com (Linux)
If you use this example, the ping will exit in 20 seconds. It will terminate regardless of the number of packets send or received.
Constant ping – ping –t google.com (Windows) ; ping google.com (Linux and macOS)
It will run without stopping. Endless loop. On Linux and macOS, it runs forever by default. You can stop it with Ctrl+C.
Extra tip
Did you know that you can use the ping command online, straight from your browser? This can come in handy if you only have a mobile phone around.
Just google it, and you will see more than a few sites. If you decide to use it in this way, please make sure that the site you visit is safe, and it is not going to harm your device or personal data in any way.
Common Ping Errors and Their Meanings
When using the Ping command, you may encounter several error messages that can help diagnose network issues. Understanding what these errors mean is key to resolving connectivity problems. Below are some of the most common errors:
- Request Timed Out
This error occurs when the Ping command does not receive an ICMP Echo Reply within the specified timeout period (usually 4 seconds). It may indicate that the destination device is down or ICMP packets are being dropped due to a firewall or security policy. Network congestion or packet loss along the route can also result in this error.
- Destination Host Unreachable
This message suggests that the device you are trying to reach is not accessible from your current network. Possible causes include an incorrect IP address, a network segment failure, or an issue with the gateway (router) that prevents traffic from reaching the target. This error typically comes from a router or gateway device along the path.
- General Failure
A “General Failure” error in Windows indicates a local issue, often with the network stack or configuration. It could be caused by a misconfigured TCP/IP stack, a malfunctioning network adapter, or incorrect network settings (like static IP conflicts). A system reboot or resetting the network settings is usually required.
- TTL Expired in Transit
The “TTL Expired” error occurs when the TTL (Time to Live) value of the packet reaches zero before it reaches its destination. This typically happens due to a routing loop, where the packet keeps circulating between routers without reaching the destination. A misconfigured router or a network routing issue is usually the cause.
- Ping: Transmit Failed
This error typically indicates that the ICMP request could not be transmitted from your device. Causes may include issues with the network interface card (NIC), problems with the network driver, or a misconfigured firewall blocking ICMP traffic. Checking the NIC settings or disabling firewalls temporarily can help identify the issue.
By analyzing these errors, you can pinpoint where the problem lies, whether it’s local, network-wide, or with the destination server.
Conclusion:
The ping is not the most sophisticated tool, but it is incredibly handy thanks to the fact it works on any device. Using it, you can quickly diagnose different part of the network and find the problem. You can also check our previous article and find more useful tools in our article Тools – DNS trace, Ping, Traceroute, Nslookup, Reverse lookup.