UDP (User Datagram Protocol) is one of the well-known protocols in network communications. Thanks to it, we are able to watch video streaming platforms, communicate with video calls, and play numerous games. Let’s dive deep and explain a little bit more about it!
Table of Contents
What is User Datagram Protocol?
The short acronym UDP stands for User Datagram Protocol, and it is a communication protocol applied across the Internet. It sets low-latency and loss tolerating connections between the different applications.
UDP offers fast communication due to the fact it allows data transfer before the receiving party provides an agreement. Therefore, UDP is highly valuable in communications that require speed and are considered time-sensitive. For example, Voice over IP (VoIP), Domain Name System (DNS) lookup, and video or audio playback.
Yet, this protocol is prone to data packet loss during travel from the source to the target destination. As a result, it could create some difficulties with the data transfer and makes it easy for cybercriminals to execute a Distributed Denial-of-Service (DDoS) attack.
History of UDP
User Datagram Protocol (UDP) emerged in the 1980s as part of the TCP/IP suite. It was initially developed for the ARPANET project, also known as the precursor to today’s internet. Created by David P. Reed and others, UDP was designed for simplicity and efficiency in transmitting datagrams, making it ideal for applications where speed and low overhead are priorities.
Unlike TCP, UDP does not guarantee delivery or order of packets, nor does it manage connections. This lack of reliability allows UDP to be lightweight, making it suitable for real-time applications like video streaming, online gaming, and voice-over IP (VoIP).
User Datagram Protocol gained fame due to its use in early internet protocols and applications, including DNS (Domain Name System) and DHCP (Dynamic Host Configuration Protocol). Nowadays, it continues to be widely used in various networked applications where low latency and reduced overhead are critical.
Despite its simplicity, UDP’s lack of error correction and flow control means it’s vulnerable to packet loss and out-of-order delivery. However, its efficiency and speed make it necessary in many networking scenarios, complementing TCP’s reliability with a lightweight alternative for specific use cases.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
How does it work?
UDP (User Datagram Protocol) acts in a simple way by transferring data between two devices in a network. It transmits packets (datagrams) straight to the target device without setting a connection, specifying the packets’ order, or examining if they are delivered as arranged.
Compared to TCP (Transmission Control Protocol), UDP provides more speed, yet it is not so reliable.
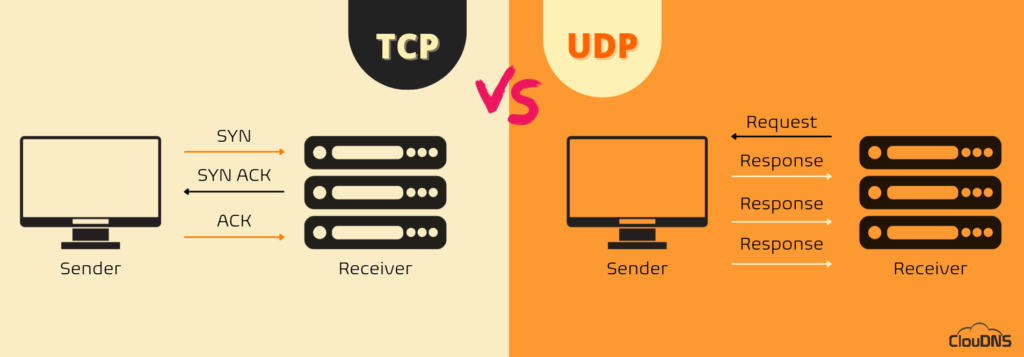
TCP communication involves a process known as a “handshake,” which establishes the connection. In addition, only when it is completed the transfer of data packets could happen.
On the other hand, the UDP connection is not including this “handshake” process which means one device simply starts sending the information to the receiving one. Additionally, UDP communications do not include details about the order or confirmation for the arrival of the data. It is exactly the opposite when it comes to TCP.
Based on these characteristics, UDP has the ability to transfer data packets a lot faster than TCP.
The downside of a UDP connection is the loss of packets during the transit, which is not going to be resent as they are in TCP connections. Therefore, when applications implement UDP, they should be able to tolerate losses, duplications, or errors.
TCP Monitoring vs. UDP Monitoring
UDP header
UDP (User Datagram Protocol) operates with headers. It uses them for packaging the message data to be sent over the network. Each UDP header includes several parameters, also known as fields, which are determined by the technical specifications of the protocol.
The UDP (User Datagram Protocol) header contains four main fields. Each of them is 2 bytes. The UDP header has the following fields:
- Source port – It is 16-bit data that specifies the precise port which is going to send the packet. In case the target device doesn’t need to reply to the sender, this field could be set to zero.
- Destination port – It is 16-bit data that serves to specify application-level service on the target device, meaning the port of the device receiving the data. It could be between 0 and 65,535.
- Length – It defines the entire number of bytes, including the UDP header and the UDP data packets for transfer. The precise limit for the UDP length field is defined with the underlying IP protocol utilized to send the data.
- Checksum – It is a 16-bits field, an optional field. The checksum gives the ability for the receiving device to confirm the integrity of the packet header and payload. It is an optional field, meaning if the application wants the checksum or not. In case it doesn’t want the checksum, then all of the 16 bits are zero. In UDP, the checksum field is used for the header and data part. In IP, the checksum field is used only for the header field. It is optional in IPv4, yet it is required in IPv6.
UDP Port
A UDP port is a numerical identifier used to distinguish different applications and services that communicate over the User Datagram Protocol (UDP). Ports allow multiple applications to send and receive data on the same device without conflicts.
UDP ports are 16-bit numbers, meaning they range from 0 to 65,535. They are categorized into three groups:
- Well-Known Ports (0-1,023): Reserved for common services. For example, DNS – port 53, NTP – port 123, DHCP – ports 67 & 68.
- Registered Ports (1,024-49,151): Assigned to specific applications, such as VoIP services and game servers.
- Dynamic/Private Ports (49,152-65,535): Used for temporary client-side communications.
Unlike TCP ports, which require an established connection, UDP ports remain stateless, meaning no persistent session exists between sender and receiver. This makes UDP faster but less reliable, as there is no built-in mechanism to verify packet delivery.
Common uses of UDP ports include streaming, VoIP, DNS queries, online gaming, and time synchronization. To improve security, firewalls often filter or block unnecessary UDP ports to prevent DDoS attacks and unauthorized access.
To check open UDP ports, administrators can use tools like:
netstat -an | grep UDP
or
nmap -sU <IP>
Understanding UDP ports is crucial for network security, troubleshooting, and optimizing communication protocols.
Applications relying on UDP
Gaming, voice, and video
The User Datagram Protocol is a great choice for various different network applications that require minimum latency, like gaming, voice, and also video communications. Services like these will not lower their quality if some of the data packets are lost during the transfer. Yet, despite the lost packets, there is a chance to implement techniques for further error correction and improvement of the audio and video quality.
Domain Name System Lookups
DNS queries are small and simple requests which receive basic and straightforward answers. A device initiates a DNS query to the DNS servers for receiving essential information about a domain, like the IP address (IPv4 or IPv6). The process is on hold until the DNS query receives its reply. Due to the fact that TCP uses a three-way handshake procedure, it means the request is probably going to be answered very slowly. As a result, it will affect the performance in a negative way. For that reason, DNS queries rely on UDP for quick answers.
Multicasting
Another way for implementing UDP (User Datagram Protocol) is for multicasting. That is based on the fact it supports packet switching. Moreover, this network protocol could also be implemented for additional routing update protocols, for instance, Routing Information Protocol (RIP).
UDP vs. TCP – what are the differences?
Let’s explain a little bit more about what are the main differences between these two protocols:
- Type of protocol
Both TCP and UDP are transport layer protocols. However, there is a main contrast between them. TCP is a connection-oriented protocol. On the other side, UDP is a connectionless protocol. So, simply TCP needs to establish the connection before the communication, while UDP does not need to ensure that the two devices have a connection.
- Reliability
TCP is considered a reliable protocol based on the fact it ensures the delivery of the data packets. It involves an acknowledgment mechanism, in which the sender gets the acknowledgment from the receiver and examines if it is positive or negative. In case it is positive, the data has been delivered successfully. If it is negative, TCP is going to resend the data.
UDP is considered an unreliable protocol based on the fact it does not provide any guarantee that the delivery of the data has been successful.
- Flow Control
TCP involves a flow control mechanism. It makes sure that an extensive number of packets are not sent to the target device simultaneously. On the other hand, UDP does not implement this flow control mechanism at all.
- Ordering
TCP operates with ordering and sequencing techniques. That way, it guarantees that the data packets are going to be delivered in the absolutely exact order in which they were sent. On the other side, UDP does not involve any ordering and sequencing techniques. That means the data could be transferred in any order.
- Speed
As we mentioned, the first step for TCP is to build the connection between the two devices. Additionally, it completes a check for errors and makes sure that the transmission of the data packets is successful. On the other hand, UDP does not build a connection or ensure the transmission. For that reason, UDP is way faster than TCP.
- Flow of data
When we speak about TCP, it offers the full-duplex service. That means the information is able to flow in both directions. Additionally, when we take a look at UDP, it is more fitting for the unidirectional flow of data.
Is UDP secure?
UDP (User Datagram Protocol) serves a great purpose for applications that tolerate packet loss. That is not an issue. Yet, based on the fact that UDP is a connectionless protocol and it does not implement a “handshake” procedure provides an opportunity for cybercriminals. They take advantage of that by flooding their victim with UDP traffic. Attackers do not need to establish a connection and receive permission for initiating such a DDoS attack.
Usually, the UDP flood attack involves sending a massive amount of UDP datagrams to different ports on the victim’s device. That causes the victim to answer with the same amount of ICMP packets indicating that these ports are unreachable. As a result, the victim’s resources are exhausted, and the DDoS attack is completed.
Thankfully there are different ways to protect your device, network, server from such malicious attempts.
- You can limit the response rate of ICMP packets. However, you should know that this could filter out legitimate packets too.
Suggested page: Explanation of ICMP Ping traffic monitoring
- A robust network of many servers (such as Anycast DNS) is a great way to prevent a single server from being drowned with malicious requests.
- Especially for your DNS network, it is a great approach to implement DDoS protection.
Advantages and Disadvantages of UDP
By understanding the main advantages and disadvantages of User Datagram Protocol, you can determine if it is the right protocol for your application. So, let’s take a closer look at what this interesting protocol can offer.
Advantages of UDP
The User Datagram Protocol provides several benefits, which are the following:
- Fast: It does not require the establishment of a connection before transmitting data, which makes it faster than TCP.’
Suggested page: Explanation of TCP monitoring - More efficient: UDP is a lightweight protocol that requires less overhead than TCP.
- Suitable for real-time applications: User Datagram Protocol is ideal for real-time applications, such as online gaming, video conferencing, and live streaming, where speed is more important than reliability.
Disadvantages of UDP
The main drawbacks of the User Datagram Protocol include the following:
- No reliability: It does not guarantee the delivery of packets or guarantee that packets will arrive in order.
- No congestion control: UDP does not have congestion control mechanisms, which means that it can flood a network with packets if not used carefully.
- Limited use cases: User Datagram Protocol is not suitable for applications that require reliable data transmissions, such as file transfers, email, or web browsing.
Suggestes article: Secure File Transfer Protocol (SFTP) Explained
UDP monitoring from ClouDNS – What is it and how to use it?
UDP monitoring is a type of network monitoring that involves scanning a selected UDP port number on a given IP address to check the availability of a service or application. Suppose the monitoring system is unable to establish a connection with the selected port. In that case, it marks the check as DOWN, indicating that the service is unavailable or experiencing issues. UDP monitoring is extremely helpful for identifying potential network problems or service disruptions before they affect end users. In addition, it allows network administrators to quickly diagnose and resolve issues, ensuring that critical services are available and performing optimally.
Conclusion
For sure, the development of UDP (User Datagram Protocol) is revolutionary. It allows fast delivery, which is highly valuable for a number of applications. UDP finds its purpose in many services despite the fact it has some downsides, mainly in DNS, video streaming, and gaming.