What is SNMP Vulnerability? How to stay protected?
SNMP Vulnerability is a hidden risk lurking in many network infrastructures. The Simple Network Management Protocol (SNMP) is a powerful...
HTTP flood attack – What is it and How to prevent it?
In a world where an online presence is crucial, an HTTP flood attack poses a significant threat, overwhelming websites with an onslaught of...
Botnet – what is it, and how does a Botnet attack work?
Cybercriminals often use Botnet for their malicious purposes. That way, they build their army of...
Understanding SYN flood attack
Imagine a tech gremlin relentlessly hammering at the door of a server, bombarding it with so many requests that it can’t keep up and...
How does OSI Application layer 7 DDoS attack work?
As cyber threats evolve, Distributed Denial of Service (DDoS) attacks have become more sophisticated and stealthy. Among the most complex...
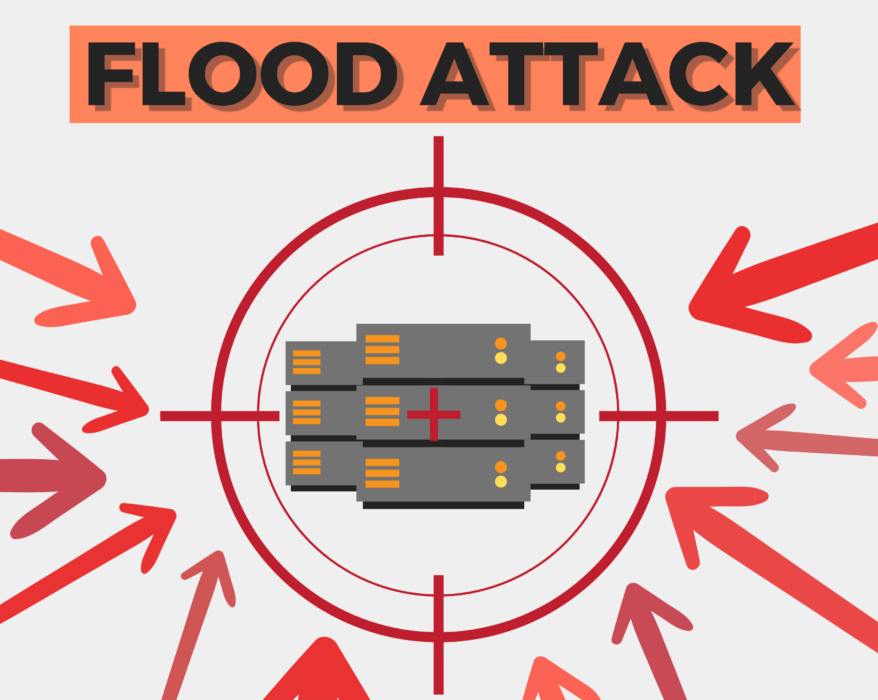
Flood Attack: Prevention and Protection
In today’s digital age, security breaches and cyberattacks have become increasingly common....
DDoS amplification attacks by Memcached
In our increasingly interconnected world, cybersecurity threats continue to evolve, and one particularly concerning method is the Memcached...
What is a Point of Presence (PoP) and Why Does It Matter?
Every time you visit a website, stream a video, or access an online service, your request travels through multiple network points before...
What is a Smurf DDoS attack?
Yes, the Smurf attack sounds cute and harmless, but we can assure you it is not. Instead, it is yet...