DDoS attacks are getting stronger, and they happen more often every year. With the advancement of technology, there are many more connected devices out there. Billions of mobile phones and many “smart” connected gadgets are easily hackable. As IoT (internet of things) is getting more popular, but not secure enough, this danger will keep rising.
Table of Contents
What are the DDoS attacks
Cybercriminals are hijacking many random connected devices around the world. The already corrupted devices are called botnets, it is a network that is waiting for instructions from the person in control. The hacker can instruct them to generate traffic to a specific target. The massive number of those devices cripples the defense of the target and brings it down.
Spamhaus 2013
Back in 2013 this was the biggest attack of its time. The website of anti-spam company Spamhaus was down on 18.03.2013 due to a large layer 3 attack. Their servers couldn’t manage the load. The attack was around 75Gbps and back then this was unimaginable (currently there are some with more than 600Gbps). They manage to stop it by signing for Anycast service.
Ready for ultra-fast DNS service? Click to register and see the difference!Experience Industry-Leading DNS Speed with ClouDNS!
BBC DDoS Attack 2015
A few years ago, on October 21st, 2016, the DNS provider Dyn was struck by a massive DDoS attack. Their servers were down, and for some time, big websites that they were hosting like Amazon, Netflix, Twitter, Reddit and more were out. The culprit of the attack was a botnet called Mirai which was made mostly from IoT devices. The attack had a cascading effect on internet services globally, drawing attention to the vulnerabilities inherent in centralized DNS providers and spurring investment in DDoS mitigation technologies.
Dyn DDoS attack 2016
A few years ago, on October 21st, 2016, the DNS provider Dyn was struck by a massive DDoS attack. Their servers were down, and for some time, big websites that they were hosting like Amazon, Netflix, Twitter, Reddit and more were out. The guilty of the attack was a botnet called Mirai which was made mostly from IoT devices.
Kerbs on Security 2016
In September 2016 just before the Dyn accident, there was another involving the Mirai botnet. The attack was very strong at around 665 Gbps, but that to the Kerbs’s security, they manage to resist it.
The Mirai botnet responsible for the attack was especially alarming for its utilization of Internet of Things (IoT) devices like cameras and routers. This marked one of the first times a botnet had so effectively leveraged commonly used household devices to orchestrate a large-scale DDoS attack.
Blizzard DDoS attack 2017
If you are a gamer, you probably know Blizzard Entertainment, the brand behind Overwatch, World of Warcraft, StarCraft, and Diablo. This company has experienced many attacks over the last years. Most noticeable was in August 2017. Many gamers were unable to connect to their server and play. These attacks are damaging the image of the company and the satisfaction of their clients.
Memcached attacks of March 2018
March was a horrible month. We saw new attacks with a larger than ever before scale. There were two that set a record, the one that hit Arbor Networks with 1.7Tbps traffic and the other that hit GitHub with 1.35Tbps a few days earlier. They both exploited the UDP port 11211. The UDP doesn’t use verification and that is the reason this was possible.
DDoS amplification attacks by Memcached
The different attacks of 2019
In 2019 we didn’t see huge attacks with +1Tbps power, but it wasn’t safe either.
Yes, there were some strong attacks of around 0.5 Tbps, but we paid attention more to the number of packets per second. In this kind of attack, the criminals do a little work, and the target does a lot of work. This is why they are called asynchronous. The attackers send small packets and receive big ones. The processing occupies the target’s resources.
Clients of Imperva had a rough start of the year. First, a strong attack of 500 million packets a second in January. It was considered one of the largest PPS (Packets Per Second) attacks known.
Later, on the 30th of April 2019, another client of theirs got attacked with 580 million PPS.
In September 2019, there was another strong attack that was targeting Wikipedia. The popular site didn’t provide information about the magnitude of the attack, but it was down for several hours on different continents.
The AWS Attack 2020
Amazon Web Services (AWS) fell prey to a DDoS attack in February 2020, which peaked at 2.3 terabits per second. The attack was of the Connectionless Lightweight Directory Access Protocol (CLDAP) Reflection type, a common DDoS attack method that amplifies the traffic. Despite the intensity, Amazon successfully mitigated the attack, preventing any significant interruption to its services.
Cloudflare Attack 2020
In August 2020, Cloudflare, a leading DDoS mitigation service, experienced a significant DDoS attack itself. Peaking at 754 million packets per second, it became one of the largest PPS-focused DDoS attacks in history. Remarkably, Cloudflare was able to thwart the attack in seconds using automated systems. However, the incident underscored the evolving complexity of DDoS attacks, showing that even cybersecurity specialists are not immune.
2023 Trends
What can we expect this year?
- Attacks with a smaller bandwidth, but intense with a high PPS number. The cybercriminals are changing their strategies.
- Increase in the duration of the attacks. Some, they can go for weeks. DDoS protection solutions should be able to withstand longer than before.
- More sophisticated attacks. It is not just about the volume anymore. For example, the exploit can happen through a different port.
- More botnets are emerging. There is already a new version of Mirai, new botnet Cayosin, and the IoT number of devices is increasing, and with this, the number of botnet devices.
According to Cisco’s projections, the global landscape for DDoS attacks is expected to witness a significant escalation, with the number of attacks doubling to approximately 15.4 million by 2023. This alarming surge underscores the growing threat of cyberattacks and emphasizes the imperative for organizations to fortify their cybersecurity measures to safeguard against this evolving menace. Since 2018, DDoS attacks have become increasingly prevalent, highlighting the pressing need for proactive defense strategies in the digital realm.
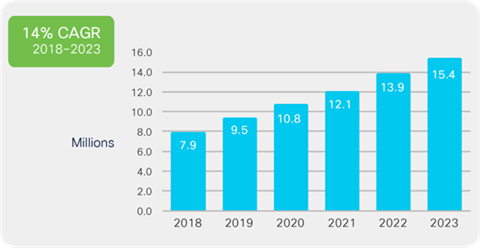
Source: Cisco Annual Internet Report, 2018–2023
How to protect from DDoS attacks?
You can use a DDoS protected DNS plan. Such a plan will include different DDoS protected servers and many Anycast locations. This will do a load balancing that will help you reduce the traffic and spread it to different servers. This way the intense wave of traffic can be reduced and your servers can withstand the DDoS attack.
Conclusion
The DDoS attack won’t stop, nor will they be lighter. If your business demands your website to be up 100% of the time, you better be prepared with the right security measures.






You should make this post like into a definitive guide or something. I bet a lot of your new readers that come to this site would want to be able to find this post. It’s too good to keep secret!