Ping of Death sounds pretty scary, and it can bring down your server and keep it that way for an extended period of time using a simple tool like the ping command. But, similar to all cyber threats, the best is to be familiar with them. So, in today’s article, we will explain in detail what Ping of Death is, how it works, and ways to prevent and stop it. Without any further ado, let’s start!
Table of Contents
Historical evolution of the Ping of Death attack
The Ping of Death (PoD) attack has a rich history. In the early days of the internet, networks and devices were less sophisticated and more susceptible to various forms of cyber attacks, including the Ping of Death. The original PoD attack involved sending malformed or oversized packets using the ICMP protocol, which could crash systems or cause network interruptions. This vulnerability was particularly prevalent in older operating systems that didn’t properly handle these packets.
Over time, as operating systems and network hardware became more advanced, they were patched to resist these types of attacks. This led to the evolution of PoD tactics, with attackers finding new methods to exploit different vulnerabilities within network protocols and systems.
What is Ping of Death (PoD)?
Ping of Death (PoD) is a popular type of DoS (Denial of Service) attack. The cybercriminal that initiates it aims to destabilize or completely crash the device, server, or service of the victim. In order to achieve that, the attacker sends malformed or oversized packets with the help of the Ping command. Unfortunately, the moment when the victim’s system processes the data packet, the system faces an error that forces it to crash.
The concept of the Ping of Death (PoD) attack is commonly compared to a mail bomb: If the recipient opens the package, a mechanism is triggered, and the target is attacked or completely destroyed.
On the other hand, the Ping command, from which the attack gets its name, is a popular tool for testing the reachability of a network. The command is designated based on the Internet Control Message Protocol (ICMP), which serves for providing status information on the Internet.
Ping of Death attacks could occur on patched and unpatched systems that have legacy weaknesses on the target systems. The cybercriminal does not even need any additional details about the target’s device or its operating system (OS). The only required information is the IP address and nothing else.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
So, now that you are familiar with what a Ping of Death attack is, it is time to dive a little bit deeper and explain how it actually works.
How does it work?
To enable a Ping of Death attack, criminals use the ping command to send oversized data packets to their target to destabilize or crash it.
An Internet Control Message Protocol (ICMP) echo-reply message, also known as “ping”, is a network utility that serves for testing a network connection. It sends out pings and waits for an ICMP echo reply, which contains information about the condition and environment of a precise network. That means the connection is successful.
In order to launch a Ping of Death attack, attackers create an ICMP packet that’s larger than allowed. The packet is separated into smaller pieces for transportation. When the receiver puts them back together, the maximum allowed size is exceeded. That leads to an overflow in the memory buffer, forcing the system to crash.
To bring it all together, the maximum packet size for IPv4 is 65,535 bytes, including a total payload of 84 bytes. Thus in order to launch a PoD attack, cybercriminals send bigger than 110k ping packets to the victim’s device.
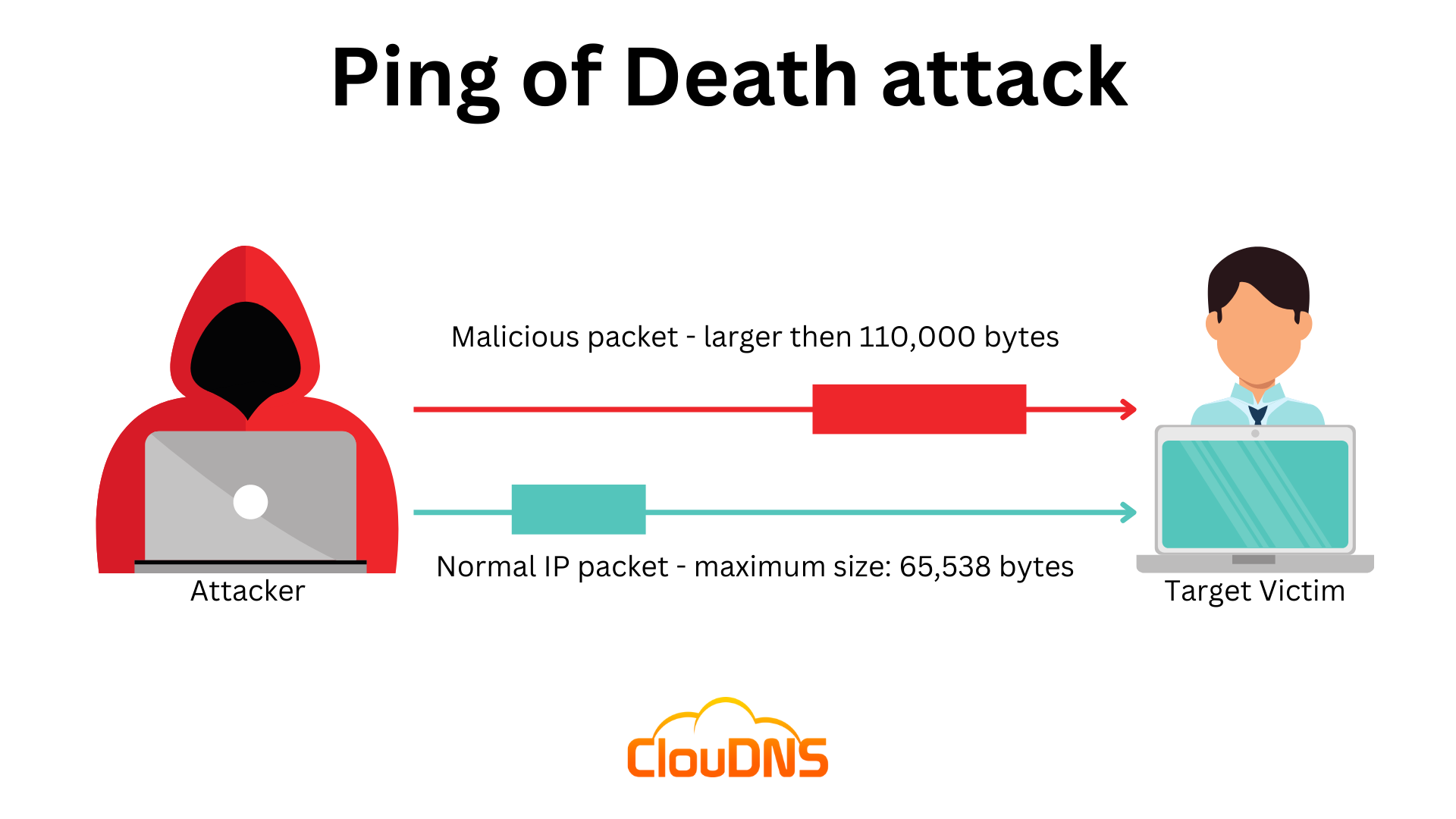
Attackers can also perform this DoS attack over the User Datagram Protocol (UDP), Internet Packet Exchange (IPX), and Transmission Control Protocol (TCP). Anything that sends an Internet Protocol datagram can be put into action.
Here’s what a Ping of Death looks like on Windows and Linux :
Ping of Death Windows:
ping <ip address> -1 65500 -w 1 -n 1
Ping of Death Linux:
ping <ip address> -s 65500 -t 1 -n 1
Does the Ping of Death still work?
The Ping of Death (PoD) is actually quite an old attack that first occurred back in the mid-1990s. Since then, the majority of devices and computers have been protected against these types of attacks. Additionally, a lot of websites keep blocking ICMP ping messages in order to stop and avoid future variations of this DoS attack.
Yet, an organization’s defenses can weaken due to malicious content on any computer, server, or network and still be vulnerable to the threat. It is threatened by this attack if the following are unpatched:
- Vulnerable Legacy Equipment
- Kernel driver in TCPIP.sys
- Windows XP and Windows Server 2013 copies on systems already vulnerable to a weakness in OpenType fonts
Recent Ping of Death attacks
Let’s explain a little bit more about some of the recent appearances of the Ping of Death attack.
- PoD attacks officially made their return in August 2013 by threatening the Internet Protocol version 6 (IPv6) networks. Then the attacker took advantage of a weakness in the soon-to-be discontinued Windows XP and Windows Server 2013 operating systems, more precisely in OpenType fonts. A flaw in the IPv6 implementation of ICMP allowed the attacker to send massive ping requests that smashed the victim when it reassembled the packets. This precise threat could have been avoided simply by disabling IPv6.
- Back in October 2020 was found a flaw in the Windows component TCPIP.sys, which represents a Kernel driver that would get to the core of any Windows system if used for an attacker’s advantage. The result would be a hard crash and total shutdown of the device, followed by a reboot. Yet, it was a bit complicated for cyber criminals to actually use this vulnerability. So, users started patching their devices in order to prevent the threat.
The Ping of Death seems to be a simple and small-in-scale attack, and that makes it an efficient weapon against particular machines. Yet, we should not underestimate it! If a group of devices comes together, there is a great chance a handful of these to bring down a website that does not have the suitable infrastructure to deal with this threat. These examples from the past indeed show that Ping of Death could still appear. Therefore, it is highly recommended for organizations to take the needed measures to protect themselves.
Preventing measures against PoD attack
There are several ways you could prevent, stop and protect yourself from a Ping of Death (PoD) attack. Most of them are easy and simple to implement. Let’s see which are they and how they can help you avoid Ping of Death.
- Configure your firewall to block ICMP Ping Messages. This will protect your network from the PoD threat, yet it will also stop legitimate pings. Additionally, invalid packet attacks can be launched through other listening ports, such as FTP (File Transfer Protocol). So, it is not an ideal solution.
- Monitoring with ICMP Ping. If you don’t like the idea of completely blocking ICMP Ping messages, Ping monitoring which is a part of the ClouDNS Monitoring service, would be your preferred solution. It spots network problems quickly and helps you improve your overall security.
Suggested article: What ICMP Ping traffic monitoring is?
- Implement DDoS Protection. A DDoS protection service provides you with a brilliant technique for network security and protecting against DDoS attacks and Ping of Death attacks.
- Update your software regularly. When a flaw appears, commonly shortly after, the patches are released too. It is important to accept them and keep your device safe.
- Implement a buffer. Improve your capability to accept large packets with an overflow buffer.
- Filter your traffic. You can stop just fragmented pings from reaching any device in the network. That will allow you to use the ping command’s utility without being at risk of an attack.
- Enable a checker in the assembly process. If it detects large bits of data, it will stop the abnormal packets and prevent crashing.
How to block Ping requests using iptables?
To block ping requests coming to and from your server using iptables, follow these instructions:
First, to reject incoming ping requests, execute the following command:
$ sudo iptables -A INPUT -p icmp –icmp-type echo-request -j REJECT
This will lead to an error message being displayed for each blocked ping. If you prefer to silently drop these requests without generating error messages, use the following commands instead:
$ sudo iptables -A INPUT -p icmp –icmp-type echo-request -j DROP
$ sudo iptables -A OUTPUT -p icmp –icmp-type echo-reply -j DROP
The first command silently blocks incoming ping requests, while the second one prevents sending out ping replies from your server.
Implementing network protocols against PoD attack
In the previous section, we examined the most popular ways to safeguard against Ping of Death attacks. Now, let’s delve into how network protocol-level measures can further fortify your defenses:
- Deep Packet Inspection (DPI): This technique goes beyond basic header analysis to examine the actual data content of packets. DPI can identify, categorize, and block packets that exhibit patterns typical of PoD attacks, such as unusual fragmentation or payload anomalies.
- Intrusion Detection Systems (IDS): IDS can be configured to recognize signatures or patterns of PoD attacks. By monitoring network traffic in real-time, IDS can alert administrators and automatically take action against suspicious packets.
- Protocol Anomaly Detection: This method involves analyzing the behavior of protocols like ICMP, TCP, and UDP against established norms. Any deviation from these norms, such as fragmented ICMP packets that could signal a PoD attack, can be flagged for further inspection or blocked.
Suggested article: Full Guide on TCP Monitoring vs. UDP Monitoring
- Stateful Packet Inspection (SPI): Unlike stateless firewalls that only examine packet headers, SPI firewalls track the state of active connections and make decisions based on the context of the traffic. This approach can effectively block malformed packets characteristic of PoD attacks.
Ping of Death vs Other Denial of Service (DoS) Attacks
The Ping of Death (PoD) attack is one type of Denial of Service (DoS) attack, but it has unique characteristics that set it apart from other DoS methods. While all DoS attacks aim to overwhelm a target and make it nonfunctional, the techniques and protocols they exploit can vary widely. Here’s how PoD compares to other common DoS attacks:
SYN Flood Attacks: In a SYN flood attack, an attacker rapidly sends SYN (synchronization) requests to a server, consuming resources by initiating many incomplete TCP connections. Unlike Ping of Death, which relies on oversized ICMP packets, SYN floods target the TCP handshake process, overloading connection capacity.
UDP Flood Attacks: UDP flood attacks use the User Datagram Protocol to send a large volume of packets to random ports on a target system, forcing it to check each request. This drains network resources as the system responds to fake requests. Unlike Ping of Death, UDP floods don’t require oversized packets. Instead, they rely on packet volume.
HTTP Flood Attacks: This attack targets web servers with high levels of HTTP requests, similar to regular web traffic. This makes the HTTP flood attack harder to differentiate from legitimate activity. PoD attacks, in contrast, are easier to detect since they involve malformed or oversized packets.
Smurf Attacks: Smurf attacks are similar to PoD in that they also use ICMP, but they work by sending spoofed ping requests to a network’s broadcast address, causing all devices to reply to the target and overload it. While both are ICMP-based, Smurf attacks rely on amplification, whereas PoD relies on oversized packets that cause system crashes.
How to Identify if Your System Is Experiencing a Ping of Death Attack
Detecting a Ping of Death attack in real-time can be challenging, as its symptoms may resemble other network issues. However, there are specific signs to watch for that could indicate a PoD attack on your system:
- Unexplained System Crashes or Reboots: One of the most direct effects of a successful PoD attack is that it causes systems to crash or even reboot unexpectedly. If your system reboots or crashes frequently with no obvious cause, it may be due to oversized ICMP packets targeting it.
- Network Connection Instability: If your network connection becomes unstable, with intermittent connectivity, it may be a sign of PoD. Because these attacks flood systems with packets that exceed the allowable size, the system can struggle to reassemble these, leading to connectivity issues.
- Memory Buffer Overflow Errors: Oversized ICMP packets can cause memory buffer overflows, which often result in error messages in system logs. Reviewing logs for buffer overflow errors related to ICMP could help you pinpoint the cause of the disruption.
- High ICMP Traffic Detected by Monitoring Tools: Network monitoring tools can help identify unusual spikes in ICMP traffic, which is a potential indicator of PoD attacks. If you see a significant increase in ping requests or ICMP packets from unknown sources, make sure to investigate further.
- Abnormal System Behavior: Sometimes, PoD attacks can cause systems to act strange, such as running slower than usual, freezing, or not responding to commands. This may be due to the processing overload caused by fragmented, oversized packets.
Best Practices Against Ping of Death
Defending against a Ping of Death (PoD) attack requires a combination of proactive system management and network-level protection. The first and most important step is to keep all operating systems and network devices up to date. Vendors regularly release security patches that fix vulnerabilities exploited by oversized ICMP packets.
Next, configure your firewall or router to filter ICMP traffic. While blocking ping requests entirely may affect legitimate monitoring, restricting or rate-limiting them reduces the attack surface without fully disabling the protocol.
Implementing a DDoS protection service is also crucial, especially for organizations that rely on online availability. These services detect and mitigate malicious traffic patterns in real time, including malformed packets typical of PoD attacks.
At the server level, enable intrusion detection systems (IDS) or deep packet inspection (DPI) to spot abnormal traffic behavior and drop malicious requests before they reach your applications.
Finally, monitor your network continuously for unusual spikes in ICMP traffic or error logs linked to buffer overflows. Early detection is critical, as it allows you to respond quickly and minimize downtime.
Conclusion
You may think that Ping of Death is outdated and it does not have a chance in modern networks. The truth is that this threat should not be neglected. It may find its way and crash your system. Therefore, it is best to take all of the precious measures in order to prevent and stop such malicious attacks.






