In today’s digital age, security breaches and cyberattacks have become increasingly common. One such form of attack is the ‘flood attack’. This type of attack can bring down services, make websites inaccessible, and compromise the overall performance of networks. In this blog post, we’ll delve deep into what a flood attack is, why it’s dangerous, how to defend against it, and its various types.
Table of Contents
What is a flood attack?
A flood attack, often a form of Distributed Denial of Service (DDoS) attack, aims to overwhelm a system with superfluous requests, thus preventing legitimate requests from being fulfilled. The primary objective is to make the target service unavailable, either by consuming all its resources or crashing it altogether. Flood attacks exploit the limitations of a network’s bandwidth, memory, and processing power. By sending an excessive number of requests, they can exhaust these resources rapidly, causing severe disruptions. Attackers often use botnets, a network of compromised devices, to generate the enormous volume of traffic required for such attacks, making it harder to trace and block the sources.
How does it work?
A flood attack works by sending a massive volume of traffic to a targeted server, service, or network. This traffic often appears to be from legitimate users, which makes it challenging to distinguish and filter out. The target system gets overwhelmed by this surge in requests, which eventually leads to its degradation or shutdown. Flood attacks can be executed through various protocols and methods, such as TCP, UDP, ICMP, and HTTP, each exploiting different aspects of the network’s communication process. Advanced flood attacks may use randomization techniques to avoid detection and mitigation efforts, making them more sophisticated and harder to counter.
Why is flood attack dangerous?
- Disruption of service: The most immediate impact is the service disruption. Websites may become unavailable, networks may slow down, and businesses may experience downtime.
- Financial impacts: With downtime comes lost revenue. Especially for businesses that rely heavily on online services, a few minutes of inaccessibility can translate to significant financial losses.
- Damage to reputation: Continuous attacks can tarnish a company’s reputation, causing loss of customer trust and loyalty.
- Resource consumption: An immense amount of resources, both human and technological, need to be diverted to handle the aftermath of such attacks.
- Diversion: Sometimes, attackers use flood attacks as a smokescreen, diverting attention from a more covert breach or intrusion.
How to mitigate it?
- Monitoring: Continuous monitoring of network traffic can help in early detection of unusual traffic spikes, which may indicate a flood attack. Tools like intrusion detection systems (IDS) can be invaluable.
- DDoS Protection: DDoS protection services can help mitigate the effects of a flood attack. These services often use a combination of traffic filtering, rate limiting, and other tactics to ensure only legitimate traffic reaches the target.
- Secondary DNS: If the primary DNS server becomes overwhelmed due to a flood attack, the secondary DNS server can continue to resolve domain names, ensuring that services remain accessible to legitimate users.
- Firewalls and Routers: Properly configured firewalls and routers can help filter out malicious traffic.
Router vs firewall - TTL Analysis: Investigate the TTL values on incoming packets. Abnormal TTLs can indicate potential malicious traffic.
- IP Blocklisting: Identify and block IPs that show malicious activity. This prevents them from accessing your systems further.
Whitelisting vs Blacklisting
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
Types of flood attack
DNS Flood Attack
A DNS flood attack specifically targets the Domain Name System (DNS) servers. The DNS is the internet’s phonebook, translating human-friendly URLs (like “example.com“) into IP addresses that computers use to identify each other on the network (like “1.2.3.4”). In a DNS flood attack, attackers send a high volume of DNS lookup requests, usually using fake IP addresses. This causes the DNS servers to try and resolve each request, leading to an overwhelming number of processes. This congestion ensures that genuine requests from real users either get significantly delayed or ignored altogether. If an attacker successfully disrupts a DNS server, it can make a whole swath of websites or online services inaccessible.
SYN Flood Attack
To understand a SYN flood attack, one must first grasp the “three-way handshake” process used to establish a TCP connection. The sequence is SYN, SYN-ACK, and ACK. In a SYN flood attack, the attacker sends a rapid succession of SYN requests but either does not respond to the SYN-ACK replies or sends them from spoofed IP addresses. The target system will keep these connections open, waiting for the final ACK that never comes. This can consume all available slots for new connections, effectively shutting out legitimate users.
HTTP Flood Attack
HTTP flood attacks take advantage of the HTTP protocol that web services operate on. In this attack, a massive number of HTTP requests are sent to an application. Unlike other flood attacks, the traffic sent looks legitimate. The requests can be either valid URL routes or a mixture with invalid ones, making them harder to detect. Because the requests look so much like typical user traffic, they’re particularly difficult to filter out. This method can exhaust server resources and cause legitimate requests to time out or receive delayed responses.
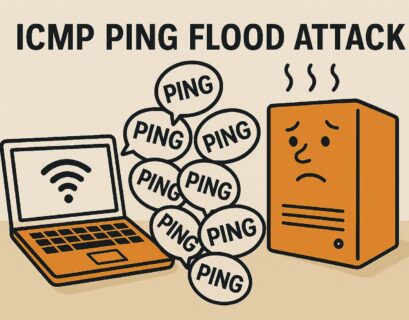
ICMP (Ping) Flood Attack
ICMP, or Internet Control Message Protocol, is a network protocol used by network devices to send error messages. The “ping” tool uses ICMP to test the availability of network hosts. In a Ping flood attack, attackers inundate the target with ICMP Echo Request (or ‘ping’) packets. The target then tries to respond to each of these requests with an Echo Reply. If the attack is voluminous enough, the target system’s bandwidth or processing capabilities may get overwhelmed, causing a denial of service.
Suggeted page: The function of ICMP Ping monitoring
UDP Flood
User Datagram Protocol (UDP) is a sessionless networking protocol. In a UDP flood attack, the attacker sends many UDP packets, often with spoofed sender information, to random ports on a victim’s system. The victim’s system will try to find the application associated with these packets but will not find any. As a result, the system will often reply with an ICMP ‘Destination Unreachable’ packet. This process can saturate the system’s resources and bandwidth, preventing it from processing legitimate requests.
Impact of Flood attacks on different industries
Flood attacks can have devastating effects across various industries, each facing unique challenges and potential damages:
E-commerce:
E-commerce platforms rely heavily on their websites for sales and customer interaction. A flood attack can cause significant downtime, leading to lost sales, decreased customer trust, and potential long-term damage to the brand’s reputation. Additionally, the costs associated with mitigating the attack and enhancing security measures can be substantial.
Suggest: Global Reach, Local Touch: The Role of GeoDNS in eCommerce Expansion
Finance:
In the finance sector, the availability and integrity of online services are critical. Flood attacks can disrupt online banking, trading platforms, and payment processing systems. This not only affects customer transactions but can also lead to compliance issues and regulatory scrutiny. The financial losses and impact on customer confidence can be severe.
Healthcare:
Healthcare providers use online systems for patient management, medical records, and telemedicine. A flood attack can interrupt these services, potentially putting patient health at risk. Delayed access to medical records and appointment scheduling can cause significant operational disruptions and affect the quality of care provided.
Gaming:
The gaming industry is a frequent target of flood attacks, especially during major events or game launches. These attacks can disrupt gameplay, causing frustration among users and leading to a loss of revenue for gaming companies. The competitive nature of online gaming also means that downtime can significantly impact player engagement and retention.
Conclusion
Flood attacks are among the oldest tools in a hacker’s arsenal, but they remain effective. As the digital landscape grows and evolves, so do the methods attackers employ. Regularly updating security infrastructure, staying informed about emerging threats, and employing a proactive defense strategy can go a long way in keeping systems secure and operational.