DDI explained in detail
It is usually possible to hear the acronym DDI commonly mentioned when discussing network...
Error 404 Explained: The Page Not Found Mystery
Every internet user has encountered the terrifying “Error 404: Page Not Found ” at some point. It’s a familiar yet...
TCP (Transmission Control Protocol) – What is it, and how does it work?
Imagine sending a message across the world and trusting it will arrive perfectly intact. That’s the magic of TCP, or Transmission Control...
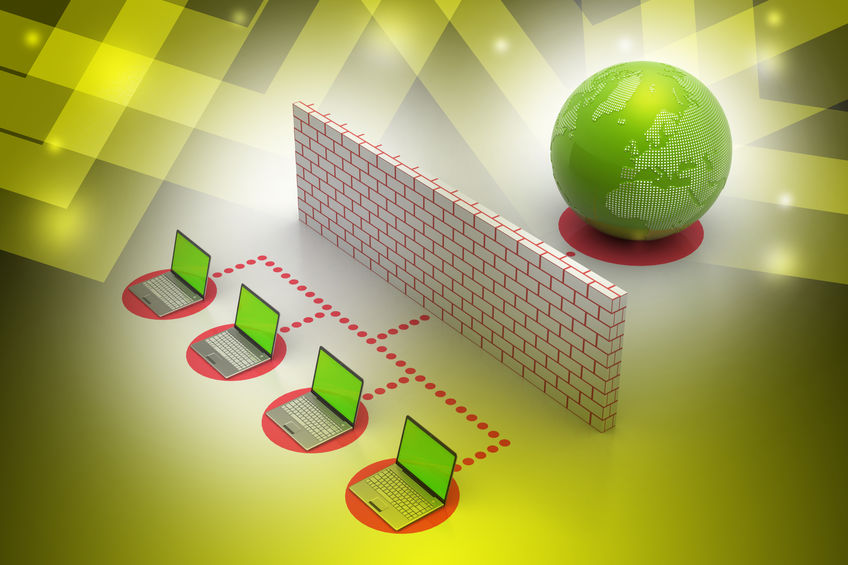
Router vs firewall, can you guess which is better?
Want to know the difference between router vs firewall? Great, you’re in the right place. In...
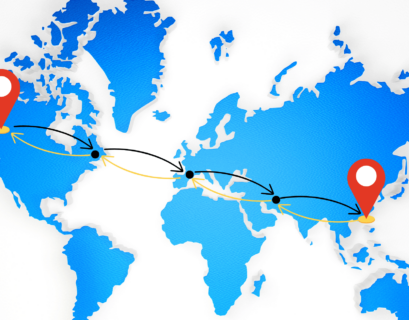
Round-Trip Time (RTT): What It Is and Why It Matters
Round-Trip Time (RTT) is a fundamental metric in the context of network performance, measuring the time it takes for data packets to...
R.U.D.Y. (R U Dead Yet) Attack Explained
In the ever-evolving landscape of cybersecurity, new threats constantly emerge, challenging the robustness of online systems. One such...
Magento, is it a good e-commerce platform?
Choosing the right e-commerce platform is one of the most important decisions any online retailer...
What is ICMP (Internet Control Message Protocol)?
The ICMP (Internet Control Message Protocol) is a network layer protocol and also a supporting protocol in the Internet protocol suite. It...
Understanding the HTTP status codes
Any now and then, when we are browsing the internet, we get one of those – error 500 or error 404. What does this number mean? How many...
Single Point of Failure (SPOF): How to Identify and Eliminate It?
The risk of a Single Point of Failure (SPOF) has become a critical concern in interconnected modern...