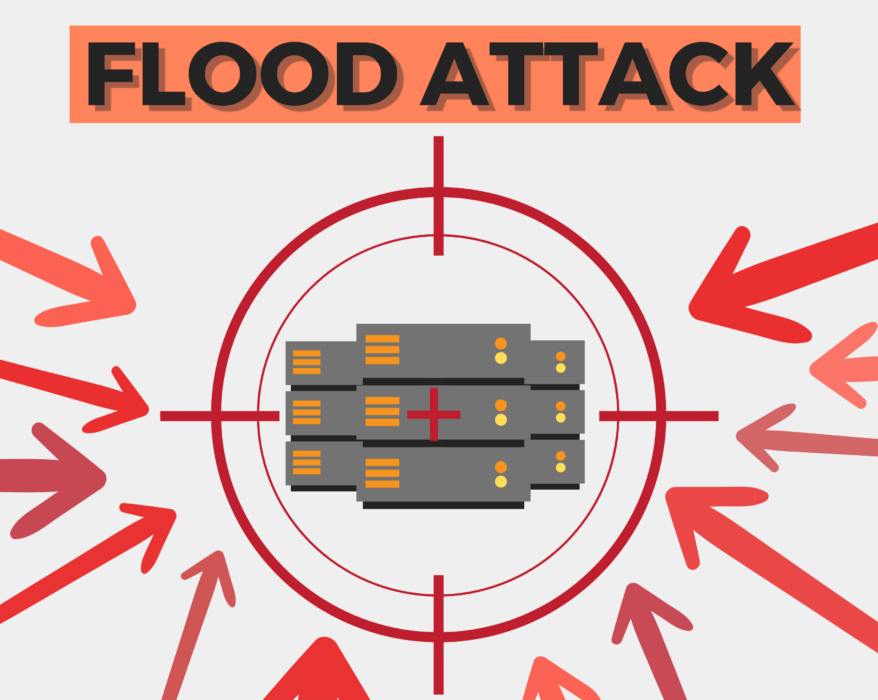
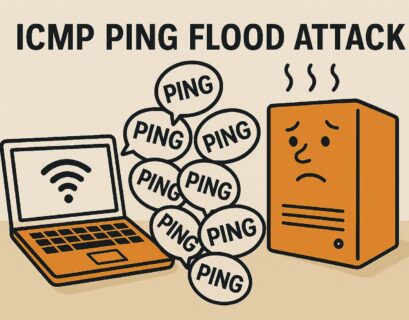
Flood Attack: Prevention and Protection
In today’s digital age, security breaches and cyberattacks have become increasingly common....
Getting Started with DNS Prefetch on Your Website
In the ever-competitive landscape of web performance, milliseconds matter. Whether you’re optimizing for Core Web Vitals, reducing...
R.U.D.Y. (R U Dead Yet) Attack Explained
In the ever-evolving landscape of cybersecurity, new threats constantly emerge, challenging the robustness of online systems. One such...
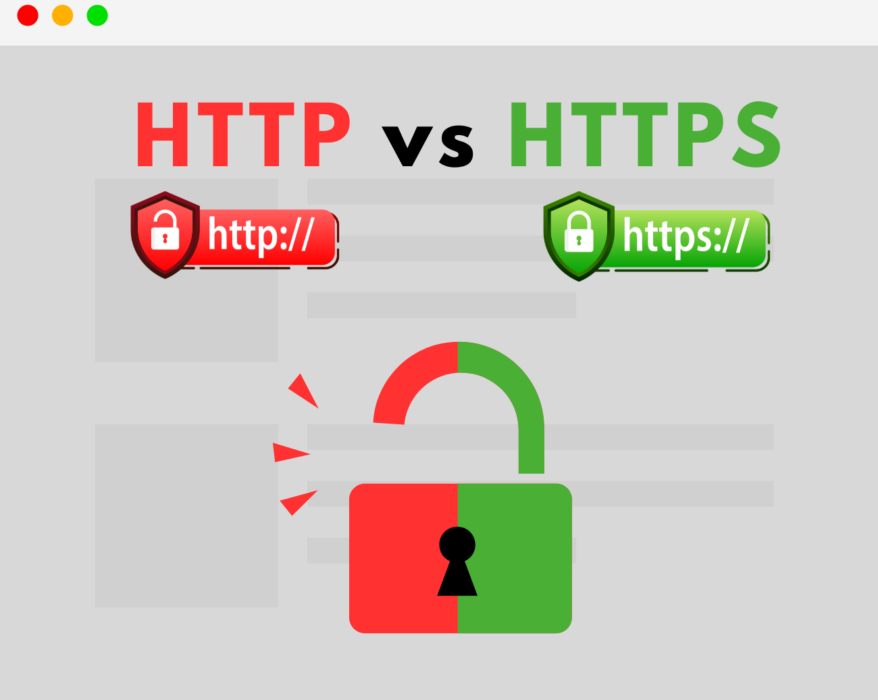
HTTP vs HTTPS: Why every website needs HTTPS today
In today’s digital age, securing information online has become more important than ever. One...
What are 301 and 302 Redirects and how to use them?
In the realm of website management and search engine optimization (SEO), proper redirection plays a crucial role in maintaining the...
What is Cybersquatting and Why Should You Care?
In the digital age, a strong online presence is essential for businesses, influencers, and...
DNS history. When and why was DNS created?
We have talked a lot about DNS. How does it work, and all the related topic around it. But we have never spent some time about the DNS...
DNS best practices
You cannot imagine the internet without DNS. There is almost no service that doesn’t depend on DNS technology. E-mails, VoIP, web...
Why media can’t live without CDN
Do you remember the time when we were reading the news in a printed newspaper and we were going to...