In a world where an online presence is crucial, an HTTP flood attack poses a significant threat, overwhelming websites with an onslaught of requests that can result in digital paralysis. This article delves into the essence of HTTP flood attacks, explaining their function and why they are a menace to web servers.
Table of Contents
What is an HTTP flood attack?
An HTTP flood attack is a form of Distributed Denial of Service (DDoS) attack specifically targeting web servers. In this malicious assault, the attacker overwhelms a web server with an enormous volume of HTTP requests, rendering it incapable of handling legitimate user requests. This tactic capitalizes on the stateless nature of the HTTP protocol, allowing for easy forging and amplification of requests. Such attacks can come from a single source or be distributed across multiple locations, making them harder to trace and block. The simplicity of executing these attacks makes them a popular tool among cybercriminals looking to disrupt online services.
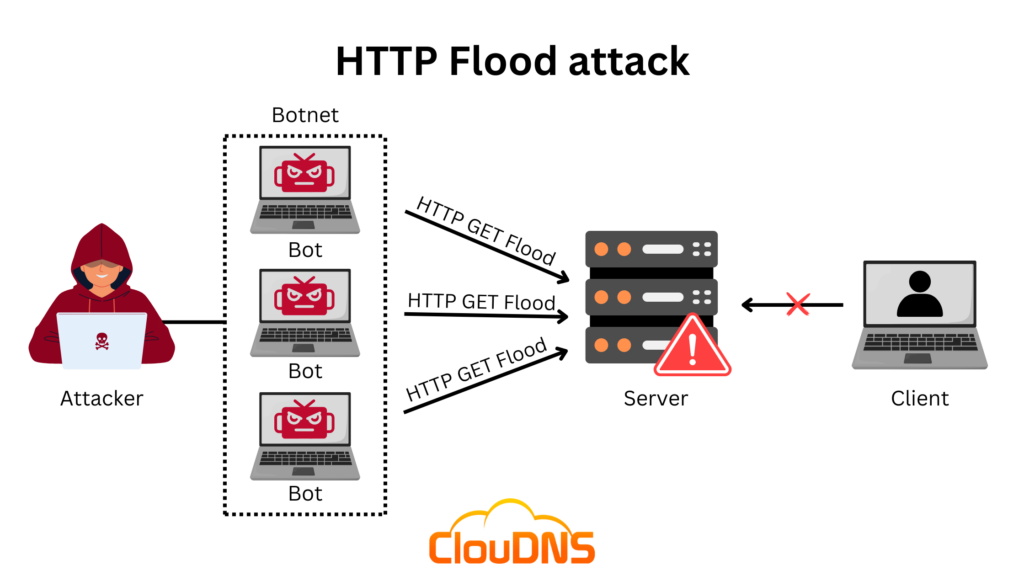
How does it work?
Step 1: Request Amplification
HTTP flood attacks exploit the stateless nature of the HTTP protocol, enabling attackers to forge a vast number of seemingly legitimate requests. These requests are often designed to consume server resources disproportionately.
Step 2: Botnet Deployment
Perpetrators commonly utilize botnets, networks of compromised computers, to amplify the scale and impact of the attack. This distributed approach makes it challenging to trace and mitigate the source of the assault.
Step 3: Targeting Specific Vulnerabilities
HTTP flood attacks may exploit vulnerabilities in web server software, operating systems, or specific applications. By pinpointing weaknesses, attackers maximize the efficacy of their assault.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
Types of HTTP flood attacks
In the realm of HTTP flood attacks, adversaries deploy a variety of tactics to overwhelm web servers, each with its own distinctive approach.
- GET Floods: GET Floods are a type of HTTP flood attack that targets the HTTP GET method used in web communication. Attackers send a massive number of GET requests to a web server, designed to look like legitimate user interactions, with the aim of overwhelming the server’s resources and capacity to respond. Imagine your website is a popular restaurant, and suddenly, an overwhelming number of customers flood in, each asking for the menu without any intention of placing an order. GET floods operate similarly, bombarding the server with a surge of requests for information, causing chaos and resource exhaustion.
- POST Floods: POST Floods focus on the HTTP POST method, which is used for sending data to a server. In these attacks, cybercriminals flood the server with numerous POST requests, often containing seemingly valid data submissions. This flood of requests can strain the server’s CPU and memory resources, causing delayed responses or service disruptions. Picture customers storming in and placing orders at an unprecedented rate, without any regard for the kitchen’s capacity. POST floods emulate this scenario by inundating the server with an excessive number of data-submission requests, pushing the server to its limits and potentially causing it to stumble.
Impact of HTTP flood attack
Picture your website as a bustling city during rush hour and an HTTP flood attack as an unexpected surge in traffic causing digital gridlock. This online congestion not only disrupts normal operations but also leads to inevitable downtime and service interruptions as the server contends with an overwhelming influx of requests.
- Downtime and Service Disruption. Think of your website as a bustling city with countless residents seeking information. An HTTP flood attack is like an unexpected traffic jam, bringing the entire city to a standstill. Downtime and service disruption become inevitable as the server struggles to handle the overwhelming surge of requests.
Suggested article: Understanding the HTTP status codes
- Financial Loss. Just as a shop loses revenue when forced to close unexpectedly, businesses hit by an HTTP flood attack experience financial setbacks. The loss isn’t just in terms of immediate revenue; it’s also about potential future earnings as user trust takes a hit.
- Reputational Damage. Consider the impact on a brand when its flagship store experiences a sudden closure. Similarly, successful HTTP flood attacks can tarnish a website’s reputation, eroding the hard-earned trust of users. Reputational damage extends beyond the immediate attack, affecting long-term relationships with customers.
5 Signs your website is under HTTP flood attack
Early detection of an HTTP flood attack is crucial for effective response. Here are technical indicators that may signal such an attack:
- Increased HTTP Request Rates: If your web server logs show a sudden and sustained increase in HTTP GET or POST requests, especially from a range of unusual IP addresses, this could indicate an attack. Monitoring tools can be configured to alert administrators to spikes that exceed baseline levels.
- Increased CPU and Memory Usage: HTTP flood attacks force the server to handle a massive number of requests, leading to unusual CPU and memory consumption. If your server resources are maxing out unexpectedly, this might be a sign of a flood attack.
- Slow or Non-Responsive Website: A significant HTTP flood attack can slow down your website or make it entirely unresponsive, as the server struggles to handle the load. If your site becomes inaccessible or experiences frequent timeouts, it may be under attack.
- Log Files Full of Repetitive Requests: When reviewing server logs, you may notice a large volume of similar requests, often with the same IP range, user agent, or request URL. This repetitive pattern is a hallmark of HTTP flood attacks, as attackers often send requests in bursts.
- Increased Bounce Rate Without Clear Cause: When legitimate users experience a slow or non-responsive website due to an attack, they are more likely to leave. If you see a sudden increase in bounce rate without an obvious reason, an HTTP flood attack may be the culprit.
Preventive measures against HTTP flood attack
Detecting an HTTP flood attack is akin to being the vigilant lifeguard at a crowded beach.
Monitoring service
Just as a lifeguard watches the ocean for irregularities, detecting HTTP flood attacks involves monitoring for abnormal spikes in web traffic. An unexpected surge signals trouble, prompting a swift response to ensure the safety of the online “beach.” With HTTP/HTTPS Monitoring service you will be able to keep track of the performance and availability of websites, web applications, and web services.
Web Application Firewalls (WAFs)
Think of WAFs as the vigilant eye of the lifeguard tower, surveying the digital sea. These firewalls analyze incoming traffic, identifying and blocking any suspicious activity, acting as a proactive defense against potential threats.
DDoS Mitigation Services
There are services specifically designed to protect against DDoS attacks, including HTTP Floods. DDoD Protection services work by diverting traffic through their networks first, filtering out the bad traffic, and only sending the good traffic to your server.
Implement Content Delivery Networks (CDNs)
CDNs distribute your content across multiple, geographically diverse servers, so it’s closer to your users. This not only speeds up content delivery but also means that traffic is spread out and not directed at a single server, making it harder for an HTTP Flood to have an impact. In addition, at ClouDNS you can build your own CDN with our GeoDNS service. With it you can be one layer protected against these malicious attacks.
How to create your own CDN using DNS
Creating Redundancies
Have a backup plan, or in technical terms, create redundancies. If one server or network component fails under the load, others can take over. This is like having backup generators ready in case the main power supply goes out.
Conclusion
Though HTTP flood attacks present a real and present danger to web servers, the good news is that they are not insurmountable. By staying vigilant, employing a layered security approach, and embracing both reactive and proactive defense strategies, businesses can effectively dampen the impact of these attacks. Ensuring your website’s resilience in the digital ecosystem is key, allowing you to maintain seamless operations and safeguard your digital assets against such disruptive forces.






