DNS hijacking is a malicious cyber attack that can have serious consequences, such as stealing your personal data or redirecting you to malicious websites. In this article, we’ll take a closer look and explain what it is, how it works, and, most importantly, how to protect yourself. From website owners to end users, we’ll explore the steps you can take to protect your online security.
Table of Contents
What is DNS Hijacking?
DNS hijacking, also known as DNS redirection, is a malicious cyber attack that redirects internet traffic away from its intended destination and redirects it to a malicious website. This is achieved by modifying the DNS server’s settings or by compromising the user’s computer or network.
When you type a website’s domain name into your web browser, your computer sends a DNS request to find the IP address associated with that domain name. In a DNS hijacking attack, the attacker replaces the legitimate IP address with their own, sending the user to a fake website that may look identical to the real one.
DNS hijacking can be used for various malicious purposes, such as phishing, stealing sensitive information, or spreading malware. Therefore, it is a serious threat to internet security and can affect anyone.
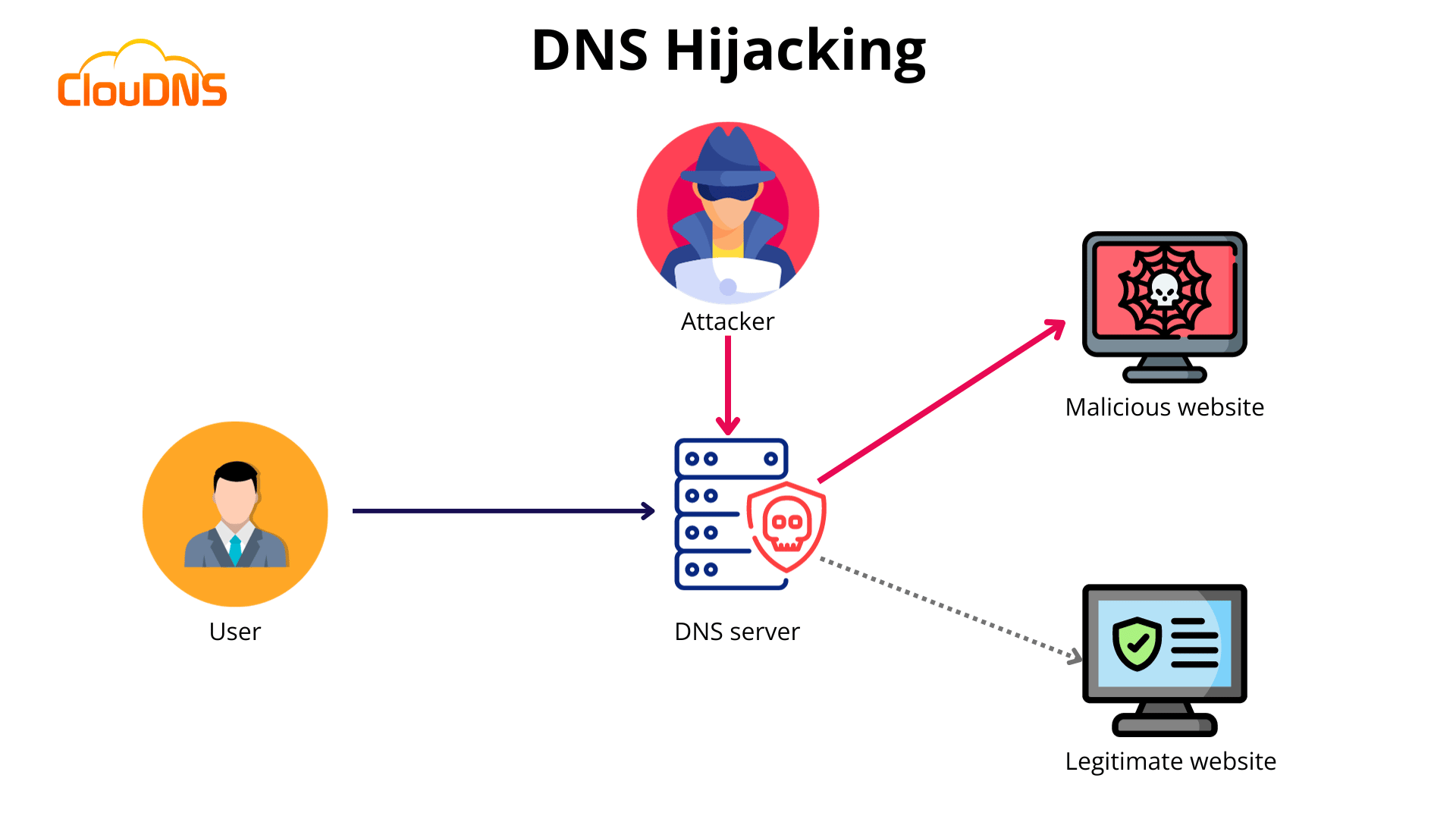
How does it work?
Cybercriminals can execute different strategies to complete their malicious goal. However, some of the main steps involved in a DNS hijacking attack are the following:
- The attacker gains access to the victim’s computer or network, either by exploiting a vulnerability or through social engineering techniques such as phishing.
- The attacker then changes the computer’s DNS settings or modifies the DNS server to point to a malicious DNS server controlled by the attacker.
- When the user tries to access a website, the request is sent to the malicious DNS server instead of the legitimate DNS server.
- The malicious DNS server responds with a fake IP address corresponding to a malicious website instead of the actual website the user intended to visit.
- The user’s computer then connects to the fake IP address and is redirected to a fake website. It usually looks like the legitimate one, yet the attacker controls it.
- The attacker can then steal the user’s sensitive information, such as login credentials, credit card details, or other personal data.
- The attacker can also use the fake website to distribute malware or launch further attacks.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
Types of DNS Hijacking Attacks
There are several types of DNS hijacking attacks that attackers may use to redirect traffic and compromise users’ security. Here are some of the most common types:
- Local DNS hijack: This type of attack involves modifying the DNS settings on a single computer or device, usually by malware. The attacker changes the DNS settings to point to a DNS server controlled by the attacker, which can redirect the user to malicious websites.
- Router DNS hijack: This attack targets the DNS settings on a router, which can affect all devices connected to the network. The attacker gains access to the router’s DNS settings, usually by exploiting a vulnerability or guessing a weak password. Then it modifies the DNS setting so that they point to a DNS server that is under its control.
- Man-in-the-middle DNS attack: It involves intercepting and modifying DNS requests and responses in transit between the user’s computer and the legitimate DNS server. The attacker can modify the DNS response to redirect the user to a malicious website or intercept sensitive information entered by the user.
- Rogue DNS Server: In this type of attack, the attacker hacks a legitimate DNS server and then modifies DNS records to redirect DNS requests to a malicious website. This can be done by exploiting vulnerabilities in the DNS software or by using social engineering techniques to gain access to the server.
How to Protect from DNS Hijacking
For Name Servers and Resolvers
Protecting name servers and resolvers from DNS hijacking is critical to ensure the security and availability of the DNS infrastructure. Here are some additional steps that can be taken to protect against DNS hijacking:
- Install Firewalls Around Your DNS Resolver: Firewalls can be used to restrict access to your DNS resolver to authorized sources only. By implementing firewalls, you can block traffic from unauthorized sources, reducing the risk of DNS hijacking.
- Increase Restrictions on Access to Name Servers: Restricting access to name servers can limit the potential attack surface for DNS hijackers. Access to name servers should be limited to only those who need it, and access should be protected with strong passwords and two-factor authentication (2FA).
- Fix Known Vulnerabilities: It’s important to keep your DNS resolver and name servers up-to-date with the latest security patches and fixes. This helps to ensure that any known vulnerabilities are addressed, reducing the risk of exploitation by attackers.
- Use encrypted DNS: Encrypted DNS protocols like DNS-over-HTTPS (DoH) and DNS-over-TLS (DoT) can help protect against DNS hijacking by encrypting DNS traffic between clients and resolvers. This makes it more difficult for attackers to intercept and manipulate DNS traffic.
- Avoid Zone Transfers: Zone transfers, which allow name servers to exchange information about DNS zones, can be used by attackers to gather information that can be used in DNS hijacking attacks. Limiting or disabling zone transfers can help prevent this type of attack.
For website owners
As a website owner, there are several measures you can take to protect your website from DNS hijacking. Here are some steps you can follow:
- Control DNS access: Limit DNS access to a selected few IT team members with multi-factor authentication when accessing the domain name server registrar. To further enhance security, whitelist only specific IP addresses to access the domain name registrar.
- Enable Client Lock: Some DNS registrars use client locks to prevent unauthorized DNS record changes. This feature disables the option to modify DNS records unless a request is made from a precise IP address.
- Choose a reputable DNS service: Choose a DNS service with a reputation for reliability and security.
- Implement DNSSEC: DNSSEC adds an additional layer of security to the DNS system. It helps prevent DNS hijacking by verifying the authenticity of DNS records. Implementing DNSSEC can protect your website from various DNS attacks, including DNS cache poisoning and man-in-the-middle attacks.
- Monitor DNS activity: Regularly monitor your DNS activity to detect any unusual activity or unauthorized changes. Set up alerts for any suspicious DNS activity, and take immediate action if any unauthorized changes are detected.
Monitoring service plans from ClouDNS
For end users
End users can also take steps to protect themselves from DNS hijacking. Here are some ways end users can protect themselves:
- Protect your internet traffic with a VPN: A fast Virtual Private Network (VPN) can help safeguard your internet traffic by encrypting it and routing it through a secure tunnel, which makes it challenging for attackers to intercept your DNS queries.
- Clear your DNS cache: Clearing your DNS cache periodically can prevent attacks that use DNS cache poisoning to redirect your internet traffic to malicious sites.
- Watch out for suspicious emails and links: Make sure not to click on links in emails from unknown senders or unfamiliar websites, as they could lead to sites that could hijack your DNS.
- Verify website security before entering sensitive data: Verify the URL of a website before entering any sensitive information. Look for the padlock icon in the address bar, which indicates that the website uses HTTPS encryption to protect your data.
- Keep your antivirus software updated: Ensure your software is updated to the latest version, as it can help detect and remove malware that may be used to carry out DNS hijacking attacks.
- Change your passwords frequently: It’s a good practice to change your passwords regularly, especially for important accounts. That way, you minimize the risk of an attacker gaining access to your accounts through DNS hijacking.
Consequences of DNS hijacking
DNS hijacking can have severe negative effects on both individuals and organizations. Here are some of them:
- Identity Theft and Fraud: The attack can redirect users to malicious websites that imitate legitimate ones. Attackers can then steal sensitive information such as login credentials, financial data, or personal information, leading to identity theft and financial fraud.
- Data Breaches: By redirecting traffic to fraudulent websites, attackers can also inject malware onto users’ devices. This malware can compromise the security of personal and sensitive data stored on the device, leading to data breaches with potential consequences for both individuals and organizations.
- Disruption of Services: DNS hijacking can disrupt the normal functioning of websites and online services by redirecting legitimate traffic to malicious servers or by causing DoS (Denial-of-Service) attacks. This can result in downtime, loss of productivity, and damage to the reputation of businesses and organizations.
- Damage to Reputation and Trust: When users encounter problems accessing a website due to DNS hijacking, they can lose trust in the affected organization’s ability to maintain a secure online presence. Customers may perceive the organization as unreliable or insecure, leading to reputational damage that can be difficult to restore.
- Financial Losses: Mitigating the effects of DNS hijacking requires direct costs, such as investigation and implementation of security measures. Apart from that, organizations may also face financial losses due to decreased customer trust, missed business opportunities, and potential legal liabilities resulting from data breaches or regulatory non-compliance.
Conclusion
In conclusion, DNS hijacking is a serious cyber attack that can have severe consequences, including stealing sensitive information and redirecting users to malicious websites. However, by being aware of the risks and taking preventative measures, you can safeguard your online security against this malicious attack.
Hello! My name is Vasilena Markova. I am a Marketing Specialist at ClouDNS. I have a Bachelor’s Degree in Business Economics and am studying for my Master’s Degree in Cybersecurity Management. As a digital marketing enthusiast, I enjoy writing and expressing my interests. I am passionate about sharing knowledge, tips, and tricks to help others build a secure online presence. My absolute favorite thing to do is to travel and explore different cultures!


