The ICMP (Internet Control Message Protocol) is a network layer protocol and also a supporting protocol in the Internet protocol suite. It is mainly used for reporting errors by different network devices, such as routers.
It helps determine if the transferred data is reaching its target destination on time. For that reason, ICMP is an essential element when it comes to the error reporting process and testing. However, it often gets utilized in DDoS (Distributed Denial-of-Service) attacks.
Table of Contents
History of ICMP
The ICMP protocol was conceived as a vital component of the Internet Protocol Suite, introduced in 1981 with RFC 792. Its origins can be traced back to the early days of the internet when the need for a diagnostic and error-reporting tool was identified. Over the years, ICMP has experienced several refinements, with additional message types being introduced. Its fundamental purpose of providing feedback about issues related to datagram processing has remained consistent throughout, making it an indispensable tool for network diagnostics.
What is ICMP protocol used for?
The ICMP protocol could be used in several different ways. They are the following:
The main purpose of ICMP is to report errors
Let’s say we have two different devices that connect via the Internet. Yet, an unexpected issue appeared, and the data from the sending device did not arrive correctly at the receiving device. In such types of unpleasant situations, ICMP is able to help. For instance, the problem is occurring because the packets of data are too large, and the router is not capable of handling them. Therefore, the router is going to discard the data packets and send an ICMP message to the sender. That way, it informs the sending device of the issue.
ICMP is commonly used as a diagnostic tool
It is used to help determine the performance of a network. The two popular utilities, Traceroute and Ping, operate and use it. They both send messages regarding whether data was successfully transmitted.
- The Traceroute command is helpful for displaying and making it easy to understand the routing path between two different Internet devices. It shows the actual physical path of connected routers that handle and pass the request until it reaches its target destination. Each travel from one router to another is called a “hop.” The Traceroute command also reveals to you how much time it took for each hop along the way. Such information is extremely useful for figuring out which network points along the route are causing delays.
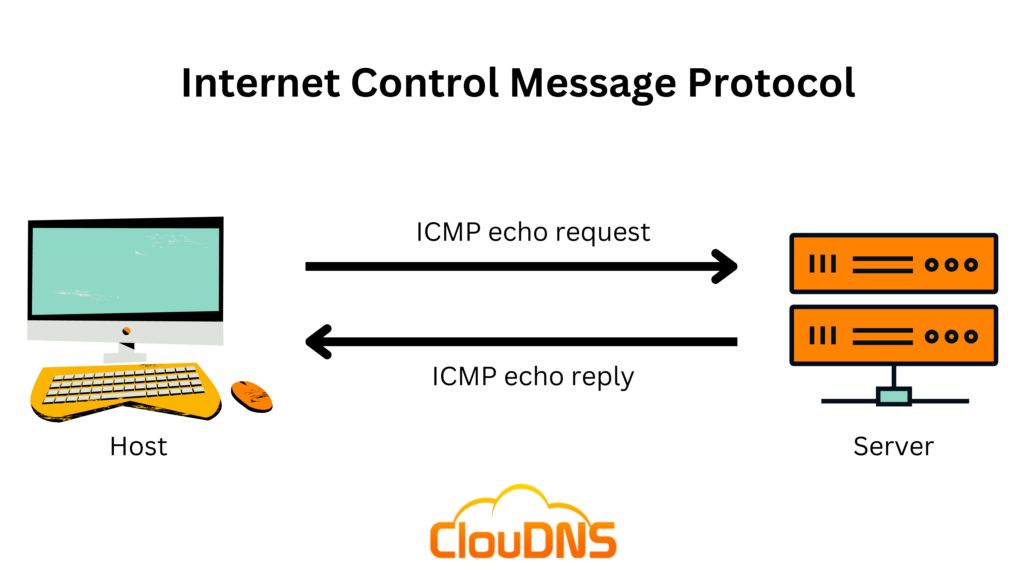
- The Ping command is similar, yet a little bit more simple. It tests the speed of the connection between two different points, and in the report, you can see precisely how long it takes a packet of data to reach its target and return to the sender’s device. Despite the fact that the Ping command does not supply additional data about routing or hops, it is still an extremely beneficial tool for estimating the latency between two points. The ICMP echo-request and echo-reply messages are implemented during the ping process.
Cybercriminals utilize it too
Their goal is to disturb the normal network performance. They initiate different attacks, such as an ICMP flood, a Smurf attack, and a Ping of death attack. Attackers are determined to overwhelm the victim and make the standard functionality not possible.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
How does it work?
Internet Control Message Protocol stands as one of the leading protocols of the IP suite. Yet, it is not associated with any transport layer protocol, for instance, Transmission Control Protocol (TCP) or User Datagram Protocol (UDP).
ICMP is one of the connectionless protocols, which means that a sending device is not required to initiate a connection with the receiving party before transmitting the data. That is why it differs from TCP, for instance, where a connection between the two devices is a mandatory requirement. Only when both devices are ready through a TCP handshake, a message could be sent.
All ICMP messages are sent as datagrams and include an IP header that holds the ICMP data. Each datagram is a self-contained, independent entity of data. Picture it as a packet holding a portion of a larger message across the network. ICMP packets are IP packets with ICMP in the IP data part. ICMP messages also include the complete IP header from the original message. That way, the target system understands which precise packet failed.
ICMP Packet Format
ICMP is designed to be used within IP packets. When an ICMP message is sent, it is encapsulated within an IP packet, and the ICMP header follows the IP header within that packet.
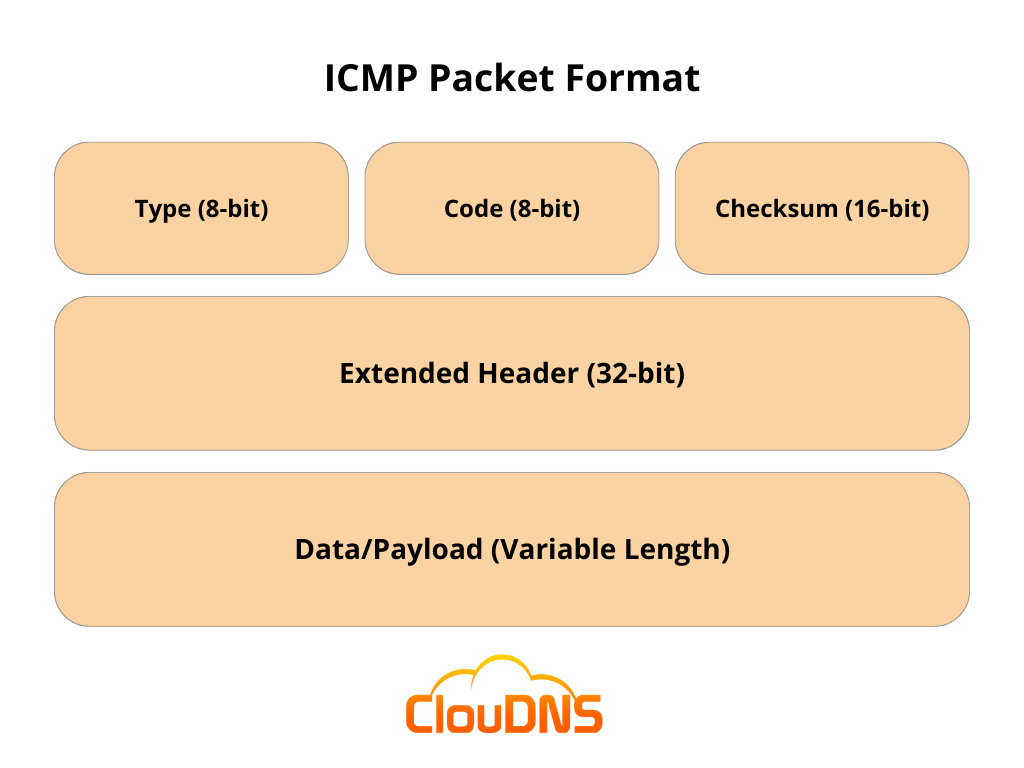
In the ICMP packet format, the first 32 bits of the packet are divided into three fields:
Type (8-bit): The initial 8 bits of the packet specify the message type, providing a brief description so the receiving network knows the kind of message it is receiving and how to respond. Common message types include:
- Type 0: Echo reply
- Type 3: Destination unreachable
- Type 5: Redirect Message
- Type 8: Echo Request
- Type 11: Time Exceeded
- Type 12: Parameter problem
Code (8-bit): The next 8 bits are for the code field, which provides additional information about the error message and its type.
Checksum (16-bit): The last 16 bits are for the checksum field, which checks the number of bits in the complete message to ensure that all data is delivered correctly.
Extended Header (32-bit): The next 32 bits of the ICMP header are the Extended Header, which points out issues in the IP message. Byte locations are identified by the pointer which causes the problematic message. The receiving device uses this information to pinpoint the issue.
Data/Payload: The final part of the ICMP packet is the Data or Payload, which is of variable length. In IPv4, the payload includes up to 576 bytes, while in IPv6, it includes up to 1280 bytes.
Types and codes in ICMP
ICMP messages are distinguished by their type and, in some cases, a code to further specify the nature of the message. There are numerous types, each serving a unique purpose. A few common types include:
- Echo Reply (Type 0): A response to an echo request, commonly used in ping.
- Destination Unreachable (Type 3): Indicates that the destination is unreachable for some reason. Various codes further specify the reason, such as network unreachable (Code 0), host unreachable (Code 1), or protocol unreachable (Code 2).
- Redirect (Type 5): Informs the host to send its packets on an alternative route. The accompanying codes provide more details, like redirect for the network (Code 0) or redirect for the host (Code 1).
- Time Exceeded (Type 11): Generated when a packet takes too long to transit a network or when reassembly time is exceeded.
These are just a few examples, and there are many other types and codes in the ICMP specification that serve various purposes.
Configuring ICMP on routers and firewalls
Configuring ICMP settings on routers and firewalls is essential to either allow ICMP traffic, prioritize it, or block it to enhance security. Here’s a brief guide:
On Routers:
- Access the router’s admin panel, usually through a web interface or command line.
- Navigate to the advanced settings or firewall settings.
- Look for an option related to ICMP or ‘Ping Request’ and either enable or disable it as required.
On Firewalls:
- Open the firewall management interface.
- Search for a rule or setting related to ICMP traffic.
- Modify the rule to allow, block, or prioritize ICMP traffic based on your needs.
It’s crucial to consult the router or firewall’s documentation or seek expert advice, as incorrect configurations might result in network vulnerabilities or communication problems.
Router vs firewall, can you guess which is better?
ICMP Port?
As we mentioned earlier, the Internet Control Message Protocol is a part of the Internet protocol suite, also known as the TCP/IP protocol suite. That means it relates only to the Internet Layer. Port numbers are only found in the Transport Layer, which is the layer above.
Although Internet Control Message Protocol does not implement the concept of ports like TCP and UDP, it utilizes types and codes. Typically employed ICMP types are echo request and echo reply (used for Ping) and TTL (time-to-live) exceeded in transit (used for Traceroute).
What is ICMP Ping?
The ICMP echo request and the ICMP echo reply messages are also known as ping messages. Ping command is a beneficial troubleshooting tool that system administrators use to test for connectivity between network devices manually. They also use it for examining for network delay and loss packets.
ICMP Ping is especially useful for performing Ping Monitoring. It works by frequently pinging a precise device. This type of check sends an ICMP echo request to a specific server or device on the network, and the device instantly answers with an ICMP echo reply. That means the connection is successful, and the target server or device is up and running without any issues.
In case the ping time, which is measured in milliseconds (ms), is prolonged, that is a sure sign of some network issues.
ICMP vs TCP
The Internet Control Message Protocol, or ICMP, has a completely different function compared to TCP (Transmission Control Protocol). Unlike it, ICMP is not a standard data packet protocol. Moreover, it is a control protocol, and it is not designed to deal with application data. Instead, it is used for inter-device communication, carrying everything from redirect instructions to timestamps for synchronization between devices. It is important to remember that ICMP is not a transport protocol that sends data between different devices.
On the other hand, TCP (Transmission Control Protocol) is a transport protocol, which means it is implemented to pass the actual data. It is a very popular protocol, thanks to its reliability. TCP transfers the data packets in a precise order and guarantees their proper delivery and error correction. Therefore, the Transmission Control Protocol finds its place in many operations, including email and file transfers. It is the preferred choice when we want to ensure ordered, error-free data, and speed is not the top priority.
Suggested page: What TCP monitoring is?
ICMP in IPv6 (ICMPv6)
With the growing adoption of IPv6, ICMP has also evolved to cater to the needs of the newer IP protocol. ICMPv6, introduced with RFC 4443, is more than just an adaptation; it incorporates various features and functionalities tailored for IPv6. For instance:
- Neighbor Discovery Protocol (NDP): ICMPv6 includes NDP, replacing the ARP (Address Resolution Protocol) used in IPv4, facilitating the discovery of neighboring devices.
- Router Solicitation and Advertisement: ICMPv6 aids in the discovery of routers in a network and can solicit advertisements from them.
- Enhanced Error Reporting: ICMPv6 offers more detailed feedback, facilitating improved troubleshooting in IPv6 networks.
As the internet continues its transition from IPv4 to IPv6, the importance and relevance of ICMPv6 will only grow, making it vital for network professionals to familiarize themselves with its intricacies.
Suggested article: IPv4 vs IPv6 and where did IPv5 go?
How is ICMP used in DDoS attacks?
DDoS (Distributed Denial-of-Service) attacks are extremely popular cyber threats. They are initiated with the main goal to overwhelm the victim’s device, server, or network. As a result, the attack prevents regular users from reaching the victim’s services. There are several ways an attacker can utilize ICMP to execute these attacks, including the following:
- ICMP flood attack
ICMP flood, also commonly called Ping flood attack, attempts to overwhelm the target device with ICMP echo request packets. That way, the victim device is required to process and respond to each echo request with echo reply messages. That consumes all of the existing computing resources of the target and prevents legitimate users from receiving service.
- Ping of death attack
The Ping of Death attack appears when a cybercriminal sends a ping larger than the maximum permitted size for a packet to a victim device. As a result, the device crashes. The large packet is fragmented on its way to the victim. However, when the device reassembles it into its original, the size exceeds the limit and causes a buffer overflow.
The Ping of Death is considered a historical attack that does not appear anymore. Yet, that is not completely true. Operating systems and networking equipment that is more aged could still become a victim of it.
- Smurf attack
The Smurf attack is another common threat where the cybercriminal sends an ICMP packet with a spoofed source IP address. The network equipment responds to the packet and sends the replies to the spoofed IP, which floods the target with large amounts of ICMP packets.
Just like the Ping of Death attack, the Smurf attack should not be disregarded. Unfortunately, in a lot of different companies and organizations, the equipment is a bit aged, and the threat is real!
ICMP Tunneling: What It Is and Why It’s Dangerous
ICMP tunneling is a technique used by cybercriminals to bypass traditional network security, like firewalls and security controls. It works by encapsulating data inside ICMP echo request and echo reply packets.
As we mentioned, ICMP is commonly used for diagnostic purposes like Ping or Traceroute, making the traffic appear harmless to most detection systems. Yet, attackers can use ICMP tunnels to exfiltrate sensitive data, establish remote shell access, or create backdoors into a compromised network.
This technique is especially dangerous because ICMP is often allowed by default for diagnostic purposes, and many networks do not inspect its payload. That makes ICMP tunneling an ideal vector for stealthy, persistent attacks.
For this reason, it’s crucial for network administrators to monitor ICMP traffic, restrict unnecessary ICMP types, and implement deep packet inspection where possible. Blocking ICMP entirely isn’t always practical, but securing it is essential.
Conclusion
The ICMP (Internet Control Message Protocol) is an incredible network layer protocol that allows devices to report errors and improve their communication. Moreover, it is a great tool for network diagnosis. It is not a surprise that a lot of administrators use it daily for a better understanding of their network with the popular utilities Ping and Traceroute. Even more beneficial is the Ping monitoring, which completes regular checks. Lastly, keep in mind to take proper supervision of your network, so it stays protected from DDoS attacks that utilize the protocol for malicious purposes.